- Java String to int
- Java int to String
- Java String to long
- Java long to String
- Java String to float
- Java float to String
- Java String to double
- Java double to String
- Java String to Date
- Java Date to String
- Java String to char
- Java char to String
- Java String to Object
- Java Object to String
- Java int to long
- Java long to int
- Java int to double
- Java double to int
- Java char to int
- Java int to char
- Java String to boolean
- Java boolean to String
- Date to Timestamp
- Timestamp to Date
- Binary to Decimal
- Decimal to Binary
- Hex to Decimal
- Decimal to Hex
- Octal to Decimal
- Java Convert Decimal to Octal
- Superclass in Java
- Java Additional Topics
- Java assert Keyword
- Java Main Method
- System.out.println()
- Java Memory Management
- Java ClassLoader
- Java Heap
- Java Decompiler
- strictfp keyword in Java
- Java UUID
- javadoc | Creating API Documention in Java
- Java JRE
- Java Object getClass() Method
- Java SE
- Java EE
- Java ME
- Java vs. JavaScript
- Java vs. Kotlin
- Java vs. Python
- Java Absolute Value
- DoubleBuffer limit() methods in Java with Examples
- Java Program to reverse tOGGLE each word in String
- Java short Keyword
- How to optimize string creation in Java
- Java long Keyword
- How to remove a particular character from a string in Java
- Open a File in Java
- Java Versions
- Sort a List in Java
- Convert byte Array to String
- Java Basics
- Java Integer getInteger() Method
- How to Compile and Run Java Program
- Package class
- How to Run Java Program in Eclipse
- Java abstract Keyword
- How to Verify Java Version
- Java boolean Keyword
- Ways to Create an Object in Java
- Java byte keyword
- How to Run a Java program in Windows 10
- Java case keyword
- Runnable Interface in Java
- Java char keyword
- Reserve String without reverse() function
- Java class keyword
- Java double keyword
- Java Keystore
- Java float keyword
- How to Take Input from User in Java
- Java int keyword
- new Keyword in Java
- Take String input in Java
- Java null reserved word
- How to Read Excel File in Java
- Java private keyword
- Read XML File in Java
- Java protected keyword
- CompletableFuture in Java
- Java public keyword
- Java ExecutorService
- Java return Keyword
- How to iterate Map in Java
- How to Return an Array in Java
- How to Sort HashMap by Value
- How to Sort HashMap in Java
- Load Factor in HashMap
- Array vs ArrayList
- HashMap vs TreeMap
- HashSet vs HashMap class
- Compare Two ArrayList in Java
- Merge Two Arrays in Java
- Print Array in Java
- Read CSV File in Java
- Remove Special Characters from String
- ArrayIndexOutOfBoundsException
- ConcurrentModificationException
- NoSuchElementException
- NumberFormatException
- How to Sort ArrayList in Java
- How to Create Object in Java
- How to Print ASCII Value in Java
- How to Generate Random Number in Java
- How to Sort an Array in Java
- How to Download Java
- How to Compare Two Objects in Java
- How to Call a Method in Java
- How to Print Pattern in Java
- How to Create Singleton Class in Java
- How to Read Character in Java
- How to Reverse a Number in Java
- Can We Overload main() Method in Java
- How to Convert Char Array to String in Java
- How to Run Java Program in CMD Using Notepad
- How to Sort String Array in Java
- How to Compare Dates in Java
- How to Take Multiple String Input in Java Using Scanner
- How to Remove Last Character from String in Java
- How TreeMap Works Internally in Java
- Java Program to Find Sum of Natural Numbers
- Java Program to Display Alternate Prime Numbers
- Java Program to Find Square Root of a Number Without sqrt Method
- Java Program to Swap Two Numbers Using Bitwise Operator
- Java Program to Break Integer into Digits
- Java Program to Find GCD of Two Numbers
- Java Program to Find Largest of Three Numbers
- How to check Palindrome String in Java
- Java Program to Calculate Area and Circumference of Circle
- How to convert String to Integer and Integer to String in java
- Java Program to Check if a Number is Positive or Negative
- How to Set CLASSPATH in Java
- Java Program to Find Smallest of Three Numbers Using Ternary Operator
- How do you swap two string variables without using third or temp variable in java
- What is Diamond Problem in Java
- Java BiConsumer Interface
- Java Program to Check if a Given Number is Perfect Square
- Java Bytecode
- Java Program to Display Even Numbers From 1 to 100
- java.io package
- Java Program to Display Odd Numbers From 1 to 100
- java.net package
- Java Program to Read Number from Standard Input
- Operator Shifting
- How to Download Minecraft Java Edition
- Perfect Number Program in Java
- Can We Override Static Method in Java
- PipedInputStream and PipedOutputStream classes
- How to Avoid Deadlock in Java
- Java DatagramSocket and DatagramPacket
- How to Achieve Abstraction in Java?
- Input from console in Java
- How Garbage Collection Works in Java
- LCM of Two Numbers in Java
- How to Take Array Input in Java
- Example of open dialog box
- Icon interface Java
- How to Create Package in Java
- java.security
- How to Print in Java
- Java SortedSet E Interface
- What is Framework in Java
- Nested Loops in Java
- Why Java is Secure?
- Hierarchical Inheritance in Java
- How to Iterate List in Java
- Java Syntax
- How to Use Eclipse for Java
- Which Package is Imported by Default in Java
- Multilevel Inheritance in Java
- Could Not Find or Load Main Class in Java
- Nested if Statements in Java
- How to Compare Two Arrays in Java
- Single Inheritance in Java
- How to Convert String to JSON Object in Java
- ChocolatesByNumbers Problem in Java
- Which is Better Java or Python
- Count a Minimal Number of Jumps from Position X to Y
- How to Update Java
- Cyclic Barrier Multithreading Java
- Difference Between C and Java
- DoubleBuffer arrayOffset() Method in Java With Examples
- How to Get Value from JSON Object in Java Example
- DoubleBuffer compareTo() method in Java With Examples
- How to Split a String in Java with Delimiter
- DoubleBuffer duplicate() method in Java with Examples
- Structure of Java Program
- DoubleBuffer flip() methods in Java with Examples
- Why We Use Constructor in Java
- DoubleBuffer mark() methods in Java with Examples
- Java Create Excel File
- DoubleBuffer slice() method in Java with Examples
- Java Interpreter
- DoubleBuffer wrap() method in Java with Examples
- javac is not Recognized
- Image Processing in Java: Image Edge Detection Operators in Digital Image Processing
- Dynamic Array in Java
- Iterating Over Enum Values in Java
- Shunting yard algorithm
- Java Program to Determine Whether a Given String of Parentheses (Single Type) is Properly Nested
- Java Destructor
- Java Program to Find How Many Fish (N Voracious Fish) Are Alive Moving Along a River | Codility Fish Solution
- Custom ArrayList in Java
- Java Program to Find the Frequency of All Duplicate Elements in an Array
- ArrayList vs HashMap
- Java Program to Find the Minimal Average of Any Slice Containing at Least Two Elements
- Java Constant
- Java Program to Find the Minimal Nucleotide from A Range of Sequence DNA
- Java Tokens
- Java Program to Find the Missing Element in a Given Permutation
- Java Xmx
- Java Tail Recursion | What is Tail Recursion?
- How to Enable Java in Chrome
- Monsoon Umbrella Problem in Java
- Java Semaphore
- StrictMath scalb() Method in Java
- Array to List in Java
- Busy Waiting in Multithreading in Java
- JIT in Java
- Count The Number of Passing Cars On the Road Problem in Java
- How to Clear Screen in Java
- DoubleBuffer allocate() method in Java With Examples
- Java IDEs
- DoubleBuffer hasArray() method in Java with Examples
- Java Logger
- Final Vs. Immutability in Java
- Reverse a String Using Recursion in Java
- Generics Vs. Wildcard in Java
- Java Program to Check Whether an Array is a Permutation
- Float Vs Double Java
- Java Program to Compute the Number of Integers Divisible By k in the Range [a..b]
- Stack vs Heap Java
- Java Program to Determine Whether a Given String of Parentheses (Multiple Types) is Properly Nested
- Abstraction vs Encapsulation
- Java Program to Find an Index of an Array Such That Its Value Occurs at More Than Half of Indices in The Array
- Top 10 Java Books
- Java Program to Find the Earliest Time When a Frog Can Jump to The Other Side of a River
- public Vs. private Keyword in Java
- Java Program to Perform LU Decomposition of a Matrix
- What is Java Used For
- Java Program to Print All the Leaders in an Array
- Bitwise Operator in Java
- Minimum Number of Bricks That Can Be Intersected Problem in Java
- SOLID Principles in Java
- NumberSolitaire Problem in Java
- Type Casting in Java
- Real-Time Example for Factory Design Pattern in Java
- Conditional Operator in Java
- Real-Time Example for Immutable Class in Java
- Ternary Operator in Java
- TapeEquilibrium Problem in Java
- Java Architecture
- REPL in Java
- Baseball Strike Out Problem in Java
- Types of Exceptions in Java
- Buying Fruits Problem in Java
- Why String is Immutable or Final in Java
- CompositeName endsWith() method in Java with Examples
- Java vs Kotlin
- CompositeName equals() method in Java with Examples
- Set in Java
- CompositeName getAll() method in Java with Examples
- Why non-static variable cannot be referenced from a static context in Java
- DoubleBuffer asReadOnlyBuffer() method in Java with Examples
- Java Developer Roles and Responsibilities
- DoubleBuffer equals() method in Java with Examples
- Types of Classes in Java
- DoubleBuffer put() methods in Java with Examples
- Marker Interface in Java
- How to Create API in Java?
- Static Function in Java
- How to Solve Time Limit Exceeded Problem in Java?
- Unary Operators in Java
- ImageIcon Class Java
- What is Advance Java
- Java CORS Error
- ArrayList Implementation in Java
- MetaClass in Java
- Convert ArrayList to String Array
- Minimum Speed to Arrive on Time problem in Java
- Hashmap vs ConcurrentHashMap
- Multiset Implementation in Java Using Treemap
- List vs ArrayList
- Multithreading Hierarchy in Java
- Map vs HashMap
- MultiValueMap in Java
- HashSet vs LinkedHashSet
- Pipes in Multithreading Programs in Java
- How TreeSet Works Internally
- Real-Time Chat Application in Java
- LinkedHashMap vs HashMap
- Real-Time Example for Serialization in Java
- Java Program to Solve Quadratic Equation
- Timestamp Operations in Java
- Scope Resolution Operator in Java
- Adding two polynomials using Linked List in Java
- Composition in Java
- Banking Application Using Multithreading in Java
- CharBuffer hasArray() method in Java
- NoClassDefFoundError in Java
- Check if One String Swap Can Make Strings Equal in Java
- Threads in Java
- DoubleBuffer get() methods in Java with Examples
- Upcasting and Downcasting in Java
- Determine Whether a Triangle Can Be Built from A Given Set of Edges
- Dynamic Polymorphism in Java
- DoubleBuffer reset() methods in Java with Examples
- Java Robot
- DoubleBuffer rewind() Method in Java with Examples
- String Pool in Java
- File Processing with Java Multithreaded
- What is constructor chaining in Java
- Merge Sort in Java
- Add elements to Array in Java
- Types of Variables in Java
- Advantages and disadvantages of Java
- Why Multiple Inheritance is not Supported in Java?
- Advantages of JavaBeans
- How Multithreading Works in Java?
- AWS SDK for Java with Apache Maven
- How to Achieve Performance in Multithreading in Java?
- How to print the Next N Leap years in Java
- AWT Program in Java
- How to Reverse a String in Java Using Different Methods?
- Boolean values in Java
- How to Send E-mail in Java?
- ByteStream Classes in Java
- Java Program to Find Pythagorean Triplets in an Array
- CharacterStream Classes in Java
- Max Product of Tree in Java
- Class and Interface in Java
- MinguoDate equals() method in Java with Examples
- ClassCast Exception in Java
- Minimum Non-Zero Product of the Array Elements in Java
- Cloneable in Java
- Multiset Interface in Java
- Constructor overloading in Java
- Package getName() method in Java with Examples
- Control Flow in Java
- Package java.time Does Not Exist
- Convert Java Object to Json using GSON
- Path getNameCount() method in Java with Examples
- Convert XML to JSON in Java
- Synchronization in Respect to Multithreading in Java
- How to avoid null pointer exception in Java
- Time Class Operation in Java
- Java constructor returns a value, but what
- XOR and OR Operators Precedence in Java
- Singleton Class in Java
- Breadth First Search or BFS for a Graph in Java
- Doubly Linked List Program in Java
- CompositeName getSuffix() method in Java with Examples
- Java 12
- CyclicBarrier Class in Java
- Association in Java
- Depth First Search or DFS for a Graph in Java
- Big data Java vs Python
- Image Processing in Java- Face Detection
- Branching Statements in Java
- JapaneseChronology prolepticYear() method in Java with Example
- Collections Sort in Java 8
- Java Program to Check if Two Strings are Cyclic Permutations of Each Other
- List vs Set in Java
- Java Program to Find Union and Intersection of Two Unsorted Arrays
- How many days required to learn Java
- Java Web Services
- Implicitly Typecasting in Java
- New Date-Time API in Java 8
- Legacy Class in Java
- Print Adjacency List for a Directed Graph in Java
- Character Array in Java
- RuleBasedCollator clone() method in Java with Example
- Equals() and Hashcode() in Java
- RuleBasedCollator compare() method in Java with Example
- Externalization in Java
- RuleBasedCollator equals() method in Java with Example
- Identifiers in Java
- RuleBasedCollator getCollationElementIterator(CharacterIterator) method in Java
- InvocationTargetException
- RuleBasedCollator getCollationElementIterator(String) method in Java
- Java Pass by Value
- RuleBasedCollator getRules() method in Java with Example
- Mutable and Immutable in Java
- RuleBasedCollator hashCode() method in Java with Example
- POJO
- Detect Cycle in a Directed Graph in Java
- Power Function in Java
- Detect Cycle in Undirected Graph Using DSU in Java
- Primitive Data Types in Java
- FieldPosition getEndIndex() method in Java with Example
- Graph Problems in Java
- Virtual Function in Java
- How to Create an Array in Java
- Difference Between C, C++, and Java
- JapaneseDate isSupported() method in Java with Example
- Java String Max Size
- Java Version Check macOS
- nth Prime Number Java
- Move all special char to the end of the String in Java
- Convert Java object to JSON
- RuleBasedCollator getCollationKey() method in Java with Example
- How to Calculate Date Difference in Java
- SimpleTimeZone setRawOffset() method in Java with Examples
- How to Improve Coding Skills in Java
- SimpleTimeZone setStartYear() method in Java
- Java Email Validation
- Transitive Closure of a Graph in Java
- Java Testing Tools
- Dice Simulator Java GUI
- Permutation and Combination in Java
- Java Program to Count All Possible Paths Between Two Vertices
- JavaCC
- Java Program to Find a Mother Vertex in a Graph
- Unique Number in Java Program
- Carriage Return in Java
- JDBC MCQ
- Java Program to Find Distance of Nearest Cell Having 1 in a Binary Matrix
- OOPs MCQ
- Java Program to Find the Number of 'X' Total Shapes
- Java Code for DES
- Reverse Level Order Traversal in Spiral Form in Java
- Pig Latin Program in Java
- Transitive Closure of a Graph Using Floyd-Warshall Algorithm in Java
- Array Rotation in Java
- Unique Paths in a Grid with Obstacles Problem in Java
- Equilibrium Index of an Array in Java
- GST emSigner Java Download
- Different Ways to Print Exception Message in Java
- Java Program to Count Number of Ways to Cover a Distance
- Copy Constructor in Java
- Java Program to Count the Number of Ways to Color the Boundary of Each Block in an M×N Table
- Why We Use Static Class in Java
- Java Program to Find the Total Number of Ways of Choosing X Men and Y Women from a Total of M Men and W Women
- What is Core Java?
- Maximum Bipartite Matching Problem in Java
- Set vs Map in Java
- Burrows - Wheeler Data Transform Algorithm in Java
- How to Create a New Folder in Java
- Counting Equal Pairs in a String in Java
- Remove an Element from ArrayList in Java
- Form Minimum Number from Given Sequence in Java
- How to Create Test Cases for Exceptions in Java
- How does the 'accessOrder' Configuration in LinkedHashMap Work in Java?
- How to Convert JSON Array to ArrayList in Java
- JapaneseChronology eras() method in Java with Example
- How to Create a Class File in Java
- Mirror Characters of a String in Java
- Java Spring Pros & Cons
- Print Shortest Path to Print a String On Screen Using Java
- Java Stack Trace
- Queries for Characters in a Repeated String in Java
- Array Slicing in Java
- URLify a Given String (Replace spaces with %20) in Java
- Flutter vs Java
- Heap Sort in Java
- Permutation of Numbers in Java
- How to Achieve Multiple Inheritance in Java
- Magic Number in Java
- void Keyword in Java
- Reference Data Types in Java
- Java assert Keyword
- Counter variable in Java
- Checked Exception in Java
- How to take Character Input in Java using BufferedReader Class
- Unchecked Exceptions in Java
- Java employee details program
- finalize() Method in Java
- Java is case sensitive explain
- Java Final Variable
- Ramanujan Number or Taxicab Number in Java
- native Keyword in Java
- Advanced Java Books in 2021
- Void Class in Java
- Fail Fast and Fail Safe Iterator in Java
- extends Keyword in Java
- How to build a Web Application Using Java
- Binary to Gray Code Using Recursion in Java
- Is Java Interpreted or Compiled?
- DecimalStyle getAvailableLocales() Method in Java with Examples
- Java Big Data Frameworks
- DecimalStyle toString() Method in Java with Examples
- Java Get Data From URL
- Decimalstyle With positivesign() Method in Java With Examples
- No Main Manifest Attribute
- DecimalStyle withDecimalSeparator() Method in Java with Examples
- Java missing return statement
- Decimalstyle withNegativesign() Method in Java with Example
- Java program to remove duplicate characters from a string
- DecimalStyle withZeroDigit() Method in Java With Examples
- JUnit test case example in Java
- Edit Distance Problem in Java
- List of logical programs in Java
- Efficiently Compute Sums of Diagonals of a Matrix in Java
- PermGen space Java
- Egg Dropping Puzzle in Java
- Unsigned Right Shift Operator in Java
- Field get() method in Java with examples
- Infix to Postfix Java
- FloatBuffer slice() Method in Java with Examples
- Memory Leak in Java
- Instance Variable Hiding in Java
- How To Write Test Cases In Java
- Java Program to Check Given Matrix is Magic Square or Not
- Java 32-Bit Download For Windows 10
- Java Program to Count All Sorted Rows in A Matrix
- FizzBuzz Program in Java
- Java Program to Find Common Elements in All Rows of a Given Matrix
- Java Graph
- Java Program to Find Maximum Difference of Zeros and Ones in Binary String
- A Java Runtime Environment JRE Or JDK Must Be Available
- Java Program to Find the Mean of Array Using Recursion
- Java Does Not Open
- Java Program to Find Whether an Array is Subset of Another Array
- No Java Virtual Machine was Found
- Java Program to Generate All N Digit Numbers Having Absolute Difference as K Between Adjacent Digits
- Java Program Number to Word
- Java Program to Sort a Matrix in All Way Increasing Order
- Types of Garbage Collector in Java
- Kth Smallest Product of Two Sorted Arrays in Java
- No Suitable Driver Found For JDBC
- Print Fibonacci Series in Reverse Order Using Recursion in Java
- AVL Tree program in Java
- Print N to 1 Without Loop in Java
- Fail-fast and Fail-safe in Java
- Program to Accept String Starting With Capital Letter in Java
- Find unique elements in array Java
- Readers Writers Problem in Java Using Threads
- Highest precedence in Java
- Reverse a Doubly Linked List Using Recursion in Java
- Java Closures
- Rod Cutting Problem in Java
- Java String Encoding
- Which Java Container is Useful for Competitive Programming?
- Prim's algorithm Java
- Word Break Problem in Java
- Quartz scheduler java
- Balanced Tree Check in Java
- Red Black Tree Java
- CollationElementIterator next() method in Java with Examples
- GC Overhead Limit Exceeded
- CollationElementIterator previous() method in Java with Examples
- Generating QR Code in Java
- CollationElementIterator setOffset() method in Java with Examples
- Delegation Event Model in Java
- CollationElementIterator setText(CharacterIterator) method in Java with Example
- Java Pair
- CollationElementIterator setText(String) method in Java with Example
- Java Profilers
- CollationElementIterator tertiaryOrder() method in Java with Examples
- Java XOR
- Count Inversions Problem in Java
- Java Flight Recorder
- FieldPosition getBeginIndex() method in Java with Example
- Bucket Sort in Java
- Indexes of Subarray Sum Problem in Java
- Automorphic Number Program in Java
- Java Program to Detect Loop in Linked List
- Java Atomic
- Java Program to Find the Value of a Number Raised to Its Reverse
- Wait vs Sleep in Java
- Java Program to Rearrange The Array in Alternating Positive & Negative Items With O(1) Extra Space
- Executor Framework Java
- Minimum Jumps to Reach the End Problem in Java
- Gregorian calendar Java
- Missing in Array Problem in Java
- int vs Integer Java
- Palindrome Linked List in Java
- What is truncation in Java
- Trapping Rain Water Problem in Java
- Peterson Number in Java
- Two Sum-Pairs with 0 Sum Problem in Java
- Sunny Number in Java
- Cloning a Stack without Using Extra Memory Using Java
- Tech Number in Java
- CollationElementIterator getOffset() Method in Java with Examples
- Java HTTP Proxy Server
- CollationElementIterator secondaryOrder() method in Java with Examples
- Java Static Constructor
- Find Triplets with Zero Sum in Java
- How to prepare for Java Interview
- Fractional Knapsack Problem in Java
- Java callback function
- IsoChronology eras() method in Java with Examples
- Java 8 vs Java 11
- Java Agent Programming
- Login Form Java
- Job Sequencing Problem in Java
- Vaadin Framework Java
- Maximum difference of Zeros and Ones in Binary String Using Java
- EJB vs. Spring
- New Features of Java 23
- Fascinating Number in Java
- Remove Loop in Linked List Using Java
- Keith Number in Java
- The Celebrity Problem in Java
- Neon Number in Java
- Validate an IP Address in Java
- Spy Number in Java
- DecimalStyle getPositiveSign() method in Java with Examples
- Delete Mid of a Stack in Java
- Visitor Design Pattern Java
- Finite and Infinite Recursion with Examples in Java
- Advantages of Python over Java
- How to Implement a Thread-Safe Resizable Array in Java
- ATM program Java
- Identical Linked List in Java
- Design Principles in Java
- Java Program to Check If Array Is Palindrome
- JSON Validator Java
- Java Program to Count Number of Hops
- Pseudocode Java
- Linked List Intersection at End Using Java
- Autobiographical Number in Java
- Merge Two Sorted Linked Lists in Java
- Emirp Number in Java
- Palindromic Partitioning of a String in Java
- Sphenic Number in Java
- Partition Equal Subset Sum Problem in Java
- Windows Programming Using Java
- Reverse a Doubly Linked List by Swapping Data in Java
- Buzz Number Java
- Rotten Oranges Problem in Java
- Duck Number Java
- Symmetric Tree in Java
- Evil Number Java
- Ways To reach the N-th Stairs| Climbing Stair Problem in Java
- ISBN Number Java
- Change Gregorian Calendar to SimpleDateFormat in Java
- Krishnamurthy Number Java
- Convert From Any Base to Decimal and Vice Versa in Java
- Vert.x Java
- Count Total Set Bits in First Natural Numbers in Java
- Bouncy Number in Java
- DecimalFormat getMaximumIntegerDigits() method in Java
- Mystery Number in Java
- DecimalFormat getMinimumIntegerDigits() method in Java
- Smith Number in Java
- DecimalFormat getMultiplier() method in Java
- Strontio Number in Java
- DecimalFormat getPositivePrefix() method in Java
- Xylem and Phloem Number in Java
- DecimalFormat getPositiveSuffix() method in Java
- Complex Java Programs
- DecimalStyle getDecimalSeparator() method in Java with Examples
- ORE Number Java
- DecimalStyle getNegativeSign() method in Java with Examples
- PalPrime Number Java
- Bitonic Point in Java| Find Bitonic Point in Given Bitonic Sequence in Java
- Twin Prime Numbers
- Circular Tour Problem in Java
- Twisted Prime Number Java
- Find Kth Node from End of Linked List in Java
- Ugly number Java
- Find Length of Loop in Linked List Using Java
- Achilles Number in Java
- Friends Pairing Problem in Java
- Amicable Pair Number in Java
- Java Program to Check if a Number is Power of 2
- Playfair Cipher Program in Java
- Java Program to Check if Binary Number is Multiple of 3
- Java.lang.outofmemoryerror: java heap space
- Java Program to Find Median in a Stream
- Banker's Algorithm Java
- Segregate 0s and 1s Problem in Java
- Kruskal Algorithm Java
- Spirally Traversing a Matrix in Java
- Longest Common Subsequence
- Swapping Pair Make Sum Equal Problem in Java
- Travelling Salesman Problem
- Tree Boundary Traversal in Java
- Difference Bitwise AND (&) and Logical AND (&&) in Java
- Best Practices to Handle Exceptions in Java
- Jumping Number in Java
- Carol Number in Java
- Lead Number in Java
- Compute The Number of Intersections in a Sequence of Discs in Java
- Lucky Number in Java
- Facing The Sun Problem in Java
- Middle Digit Number in Java
- Find The Closest Number Problem in Java
- Special Number in Java
- How to Implement a Cache Eviction Policy using TreeMap in Java?
- Passing Array to Function In Java
- Java Program to Check Geometric Progression
- Java Error
- Java Program to Count Pairs in Linked List Whose Sum is Equal To X
- Java Apps
- Java Program to Find Intersection Point in Y Shaped Linked List in Java
- Lexicographical Order Java
- Java Program to Find the Number of Provinces
- Adam Number in Java
- Lexicographically n-th Permutation of a String in Java
- Bell Number in Java
- Matrix Exponential ion Java
- Reduce Java
- Padovan Sequence in Java
- LRU Cache Implementation
- Pangram Checking in Java
- Goldbach Number in Java
- Party of Couples Problem in Java
- How to Find Number of Objects Created in Java
- Print Pattern in Java (Without Using a loop)- Starting With n, Replace n with n - 5, n−5... until n≤0
- Multiply Two Numbers Without Using Arithmetic Operator in Java
- Program to find the mid-point of a line in Java
- Sum of Digits of a Number in Java
- Roof Top Problem in Java
- Sum of Numbers in Java
- Rotate Bits Problem in Java
- Power of a Number in Java
- Solving Josephus Problem in Java
- Sum of Prime Numbers in Java
- Sort a string Lexicographically Using Triple Cyclic Shifts in Java
- Cullen Number in Java
- Calculate the Discriminant Value in Java
- Mobile Number Validation in Java
- Fermat's Little Theorem in Java
- Fermat Number in Java
- Find N-th Term in Series 2, 12, 36, 80, 150…. Using Java
- Instantiation in Java
- Find Power Set Using Java
- Difference between Error and Exception in Java
- Generate Juggler Sequence in Java
- flatMap() Method in Java 8
- Hardy-Ramanujan Theorem in Java
- How to Print Table in Java
- Moser-De-Bruijn Sequence in Java
- How to create PDF File in Java
- Multiply Two Polynomials in Java
- Mersenne Number in Java
- Newman-Conway Sequence in Java
- Pandigital Number in Java
- Serialization and Deserialization of a Binary Tree in Java
- Pell Number in Java
- Steps By Knight Problem in Java
- Java Get Post
- Stern-Brocot Sequence in Java
- Fork Join in Java
- Sum of the Sequence 2, 22, 222,… in Java
- Java Callable Example
- Sylvester's Sequence in Java
- Blockchain Java
- How to Check if a String Contains only Digits in Java?
- Design of JDBC
- Java Assignment Operators with Examples
- Java Anon Proxy
- Allocate Minimum Pages Problem in Java
- Knapsack Problem Java
- Arrange an Array in Alternate Positive Negative Elements Using Java
- Session Tracking in Java
- Compute nCr%p Using Fermat Little Theorem in Java
- What is Object-Oriented Programming?
- Find Transition Point Using Java
- Literals in Java
- Intersection of Arrays with Distinct Element in Java
- Square Free Number in Java
- Mirror Tree in Java
- What is an anagram in Java
- Recman's Sequence in Java
- What is programming
- Iterate JSON Array Java
- Java Date Add Days
- CharsetEncoder replacement() Method in Java with Examples
- Java Plot
- Convert an Iterator to a List in Java
- Javac Command Not Found
- Count Special Integers in Java
- Factorial Program in Java Using while Loop
- Find k-th Rotation of an Array in Java
- Frugal Number in Java
- Find Minimum Cost of Ropes Problem in Java
- Java Digital Signature
- Find Total Numbers with No Repeated Digits in A Range in Java
- Catalan Number in Java
- Java Program to Form Coils in a Matrix
- Partition Number in Java
- Java Program to Tile a Page Content in a PDF
- Powerful Number in Java
- Multiply Two Strings in Java
- Practical Number in Java
- Program to Invert Bits of a Number Efficiently in Java
- Chromatic Number in Java
- Reader read(CharBuffer) Method in Java with Examples
- Sublime Number in Java
- Sum of Series 1^2 + 3^2 + 5^2 + . . . + (2n – 1)^2 in Java
- Advanced Java Viva Questions
- CharsetDecoder detectedCharset() method in Java with Examples
- Getter and Setter Method in Java Example
- CharsetDecoder ischarsetDetected() method in Java with Examples
- How to convert String to String array in Java
- CharsetDecoder unmappableCharacterAction() method in Java with Examples
- How to Encrypt Password in Java
- CharsetEncoder averageBytesPerChar() method in Java with Examples
- Instance Variable in Java
- CharsetEncoder encode(CharBuffer in) method in Java with Examples
- Java File Extension
- CharsetEncoder malformedInputAction() method in Java with Examples
- Java Pi
- CharsetEncoder maxBytesPerChar() method in Java with Examples
- Java Pop
- CharsetEncoder reset() method in Java with Examples
- Types of Inheritance in Java
- Flow control in try catch finally in Java
- Untouchable Number in Java
- How to Pass ArrayList Object as Function Argument in Java?
- AES 256 Encryption in Java
- Java Program to check Involuntary Matrix
- Applications of Array in Java
- Make the String Lexicographically Larger in Java
- Example of Static Import in Java
- PushbackReader read() method in Java with Examples
- Reader read(char[]) method in Java with Examples
- Lazy Loading in Java
- SortedSet addAll() method in Java with Examples
- Rectangular Number in Java
- Convert Given Binary Tree to A XOR Tree in Java
- How to Print Table in Java Using Formatter
- Find Sum of the Series 0.6, 0.06, 0.006, 0.0006, …to n Terms in Java
- Java IdentityHashMap Class
- Invert Actual Bits of a Number in Java
- Java BF
- Java Character.isSurrogate() Method
- Java Logo
- Java Program to Check if K-th Bit is Set or Not
- Undulating Number in Java
- Mirror of Matrix Across Diagonal in Java
- Java Obfuscator
- SortedSet add() method in Java with Examples
- Java Switch String
- Check if Two Binary Trees Are Mirror in Java
- Different Ways to Achieve Pass by Reference in Java
- Banking Application in Java
- Exam Seating Arrangement in Java
- Duodecimal in Java
- Find the Largest Palindrome Divisible by K in Java
- Economical Number in Java
- How to Pass Integer by Reference in Java?
- Figurate Number in Java
- Invert k-th Most Significant Bits of N in Java
- How to resolve IllegalStateException in Java
- Java Coding Software
- Java Create Jar Files
- Java ObjectInputStream Class
- Java Frameworks
- Java StrictMath Class
- Java Initialize Array
- Mirror of n-ary Tree in Java
- java lang exception no runnable methods
- BreakIterator previous() method in Java with Examples
- Java Queue
- Super Prime in Java
- Nonagonal Number in Java
- Vertical Tree Traversal in Java
- SexagesimalFormatter in Java
- Asynchronous Programming in Java
- Sierpinski Number in Java
- Backwards Compatibility in a Software System with Systematic Reference to Java
- Vigesimal in Java
- Can We Have Multiple Main Methods in Java?
- Java Color Codes
- Check if a Tree is Isomorphic or Not in Java?
- JDoodle Java
- Convert a Binary Tree to a Threaded Binary Tree in Java
- Online Java Compiler
- Convert a Generic Tree (N-ary Tree) to Binary Tree in Java
- Pyramidal Number in Java
- Decimal Equivalent of Gray Code and its Inverse in Java
- Relatively Prime in Java
- Find the Maximum Element of Java Hashset
- Java Modulo
- Find the Sequence of Strings Appeared on the Screen in Java
- Repdigit Numbers in Java
- Functional Programming in Java with Examples
- Abstract Method in Java
- Java Multicasting (Typecasting Multiple Times) Puzzle
- Convert Text-to-Speech in Java
- SortedSet clear() method in Java with Examples
- Java Editors
- Java Program to Find the Largest Clique in a Planar Graph
- MVC Architecture in Java
- Java Program to Illustrate Use of Binary Literals
- Narcissistic Number in Java
- Java Program to Implement Control Table
- Hashing Algorithm in Java
- Left -Truncatable Prime in Java
- Escape Sequence in Java
- Minimum Insertions to Make a Co-prime Array in Java
- Java Operator Precedence
- Minimum Swaps Required to Convert a Binary Tree to a Binary Search Tree (BST) in Java
- Private Constructor in Java
- Multiply Large Integers Under Large Modulo in Java
- Scope of Variables in Java
- Passing Strings By Reference in Java
- Groovy vs Java
- Program to Convert Hexa-Decimal Number to its Equivalent BCD in Java
- Java File Upload to a Folder
- Reference Class in Java
- Java Full Stack
- Referencing Subclass Objects with Subclass Vs. Superclass Reference
- Java Developer
- Resolving Conflicts During Multiple Inheritance in Java
- Thread States in Java
- String with Maximum Number of Unique Characters in Java
- Java EE vs Node.js
- Activity Selection Problem in Java
- Java Image
- Alien Dictionary Problem in Java
- Loose Coupling in Java
- Find LCA in Binary Tree in Java
- Java Top 10 Libraries
- Find Primitive Root of a Prime Number Modulo n in Java
- Method Hiding in Java
- Find the Maximum Difference Between a Node and Its Ancestor in Java
- Java Tuple
- Linked List Components in Java
- Dijkstra Algorithm Java
- Overlapping Intervals Problem in Java
- Extravagant Number in Java
- Pair Sum Closest to 0 Problem in Java
- Reactive Programming in Java
- New Line in Java
- Right-Truncatable Prime in Java
- Return Statement in Java
- Search Pattern (Rabin-Karp Algorithm) in Java
- Order of Execution of Constructors in Java Inheritance
- Stack Using Two Queues in Java
- Cardinal Number in Java
- Advantages and Disadvantages of Inheritance in Java
- Hyperfactorial in Java
- Advantages of Inheritance in Java
- Identifier Expected Error in Java
- Build an Array with Stack Operations in Java
- Java Generate UUID
- Bus Reservation System Project in Java
- Labeled Loop in Java
- Check if a Number Has Digits in the Given Order or Not in Java
- Lombok Java
- Check if DFS Strings are Palindromes in Java
- Ordinal Number in Java
- Class Expected Error in Java
- Tetrahedral Number in Java
- Count Submatrices with All Ones in Java
- Cosmic Superclass in Java
- Counting Leaves in a Binary Tree in Java
- Shallow Copy Java
- Disadvantages of Inheritance in Java
- BiFunction Java 8
- Find Inorder Successor in Binary Search Tree in Java
- Equidigital Number in Java
- Find the Maximum Factor Score of Array in Java
- Fall Through in Java
- Find the Maximum Number of Marked Indices in Java
- Java Reserved Keywords
- Finite Automata Algorithm for Pattern Searching
- Java Vs Go
- Generate a String with Characters That Have Odd Counts in Java
- Parking Lot Design Java
- Hollow Rectangle or Square Star Patterns in Java
- Boyer Moore Java
- Java Code Explainer
- Java Security Framework
- Keytool Error java.io.IOException Incorrect AVA format
- Tetranacci Number in Java
- Largest Number At Least Twice of Others in Java
- BFS Algorithm in Java
- Maximum Nesting Depth of the Parentheses in Java
- CountDownLatch in Java
- Next Greater Node in Linked List in Java
- Counting sort in Java
- Pairwise Swap Elements of a Linked List in Java
- CRC Program in Java
- Position of Rightmost Different Bit in Java
- FileNotFoundException in Java
- Print all Palindromic Levels of a Binary Tree in Java
- InputMismatchException in Java
- Print Numbers in Ascending Order that Contains 1, 2 and 3 in Their Digits in Java
- Java ASCII Table
- Pyramid Transition Matrix in Java
- Spark Java
- Queue Using Two Stacks in Java
- Lock in Java
- Smart City Project in Java
- Segment Tree in Java
- Sum of Digit Differences of All Pairs in Java
- DTO Java
- Traffic Light Program in Java
- Why main() method is always static in Java
- Validate Stack Sequences in Java
- Bellman-Ford Algorithm Java
- What are Java Buzzwords?
- BigDecimal toString() in Java
- Zigzag Grid Traversal with Skip in Java
- .NET vs Java
- Connecting to an SFTP Server Using Java JSch Library
- Java ZipFile
- Divide Two Numbers Using Binary Search Without Using Division (/) and Modulo (%) Operators in Java
- Lazy Propagation in Segment Tree in Java
- Division Without Using the Division (/) Operator in Java
- Magnanimous Number in Java
- Final Arrays in Java
- Binary Tree Java
- Find K-th Bit in N-th Binary String in Java
- Find the Value of a Mysterious Function Closest to Target in Java
- Java Dot Operator
- Flatten a Stream of Arrays in Java Using forEach Loop
- Associativity of Operators in Java
- How to Implement a Simple Network Monitoring Tool in Java?
- Fenwick Tree in Java
- Implementing Generic Graph in Java
- How annotation works in Java
- Java Program to Check if a Binary String is a Multiple of 3 Using DFA
- How to Find Length of Integer in Java
- Java Program to Check if a Number is a Multiple of 5 Without Using / and % Operators
- Java 8 filters
- Java Program to Get the Size of a Collection and Verify that the Collection is Empty
- List All Files in a Directory in Java
- Java Program to Perform Arithmetic Operations Using Methods
- TDD Java
- Java Swing Interview Questions and Answers
- How to Get Day Name from Date in Java
- Java was Started By Returned Exit Code 1
- Zigzag Array in Java
- java.lang.NoClassDefFoundError: Could not initialize class
- Class Definition in Java
- java.text.ParseException: Unparseable Date
- Find Saddle Point of a Matrix in Java
- Maximum Number of Non-Overlapping Substrings in Java
- Non-primitive data types in Java
- Nested Ternary Operators in Java
- Pancake Number in Java
- Non-Generic Vs. Generic Collections in Java
- Pancake Sorting in Java
- Number of Ways to Rearrange Sticks with K Sticks Visible in Java
- Print Matrix Diagonally in Java
- Pascal Triangle Program in Java
- Sort Dates in Java
- Program to Convert a Set to Stream in Java Using Generics
- Carmichael Numbers in Java
- QuickSort Using Multi-threading in Java
- Contextual Keywords in Java
- Smallest Integer Divisible by K Problem in Java
- How to Open Java Control Panel
- Split Two Strings to Make Palindrome in Java
- How to Reverse Linked List in Java
- Type Safety and Type Casting in Java Generics
- Interchange Diagonal Elements Java Program
- Arrays.sort() in Java
- Java Set to List
- Quick Sort in Java
- Level Order Traversal of a Binary Tree in Java
- Built-in Exceptions in Java
- Bully algorithm in Java
- Difference Between extends and implements in Java
- Convert JSON File to String in Java
- Difference Between Collection.stream().forEach() and Collection.forEach() in Java
- Convert Milliseconds to Date in Java
- Differences Between Void and Non-Void Methods in Java
- Copy Content/ Data From One File to Another in Java
- Difference Between Compile-Time and Runtime Polymorphism in Java
- Difference Between Constructor and Method in Java
- Static variable in java
- Access Specifiers vs Modifiers
- Types of Constructors in Java
- Java vs PHP
- Difference Between Interface Variable and Class Variable in Java
- replace() vs replaceAll() in Java
- Types of Methods in Java
- this vs super in Java
- Java Set.remove() Method
- Heap implementation in Java
- Java Copy Array
- How to Check null in Java
- Java ArrayList Length
- Java Arrays Fill
- Final Class in Java
- Java Font
- Difference Between String and StringBuffer in Java
- Rotate Matrix by 90 Degrees in Java
- Difference Between Interface Variables and enums in Java
- Exception Class in Java
- Native Methods in Java
- Object Class Methods in Java
- Web crawler Java
- One-Dimensional Array in Java
- Zigzag Traversal of a Binary Tree in Java
- Thread-Safe Collections Java
- Java Get File Size
- Types of Comments in Java
- Internal Working of ArrayList in Java
- Difference Between String, StringBuffer, and StringBuilder in Java
- Java Program to Print Matrix in Z Form
- String.valueOf() Method in Java
- Vertical Order Traversal of a Binary Tree in Java
- Types of Arrays in Java
- Group By in Java 8
- LinkedList Implementation in Java
- Hashing Techniques in Java
- Remove Duplicates from Array Java
- Implement Queue Using Array in Java
- Second Largest Number in Array Java
- Java 13 Features
- Usage of super Keyword in Java
- Package Program in Java
- Calculator Program in Java
- Canonical Name Java
- Java String Literal
- Method Chaining in Java
- LCS of Three Strings in Java
- Orphaned Case Java
- Difference Between Array and Vector in Java
- Bottom View of a Binary Tree in Java
- Difference Between JIT and JVM
- Coercion in Java
- Nested switch in Java
- Dictionary Class in Java
- Socket Programming in Java
- Left View of a Binary Tree in Java
- Sort a Set in Java
- Pangram Program in Java
- String Operations in Java
- Top View of a Binary Tree in Java
- String to Char Array in Java
- Tribonacci Series in Java
- Adapter Class in Java
- Hollow Diamond Pattern in Java
- Difference Between Primitive and Non-Primitive Data Types in Java
- Normal and Trace of a Matrix in Java
- How to Copy Elements from One PriorityQueue to Another in Java
- Right View of a Binary Tree in Java
- How to Update the Value of an Existing Key in a LinkedHashMap in Java
- Dining Philosophers Problem and Solution in Java
- Increment and Decrement Operators in Java
- Shallow Copy vs Deep Copy in Java
- Java Throwable.toString() Method
- Java Password Generator
- Local Variable in Java
- Java Program for Shopping Bill
- Use of this Keyword in Java
- Lock Interface in Java
- Why Java is Object-Oriented Programming
- Convert JSON to Map in Java
- Difference Between Connected Vs. Disconnected RowSet in Java JDBC
- Convert JSON to XML in Java
- How to Create a Savepoint in JDBC
- Middle Node of a Linked List in Java
- How to Handle Large Data Transfers Efficiently in Java Networking
- Pernicious Number in Java
- How to Implement Generic LinkedList in Java
- Cohesion in Java
- Java Program to Print Alphabet Inverted Heart Pattern
- How to get UTC time in Java
- Java Throwable.setStackTrace() Method
- Jacobsthal Number in Java
- KMP Algorithm for Pattern Searching
- Java BLOB
- Why Java Does Not Support Operator Overloading
- Java Calculate Age
- Z-Algorithm (Linear Time Pattern Searching Algorithm)
- JFC Java
- Regular Expression Matching Problem
- Tribonacci Number Java
- Java Atomic Vs. Volatile Vs. Synchronized
- Bernoulli number in Java
- Getting Synchronized Map from Java HashMap
- Cake Number in Java
- Difference Between Java and Ruby
- Compare time in Java
- Java Throwable.addSuppressed() Method
- Compare Two Sets in Java
- Matrix Median Problem in Java
- Substring with Concatenation of All Words in Java
- Crown Pattern in Java
- Convert List to Array in Java
- ASCII Values in Java
- Differences Between Collection and Collections in Java
- Aggregation vs Composition
- Morris Traversal for Inorder in Java
- Java version Command
- Nim Game Java
- Morris Traversal for Preorder in Java
- Package Naming Conversion in Java
- Difference Between Arrays and Collections in Java
- Rotate a Linked List by k in Java
- India Map Pattern in Java
- Ladder Pattern in Java
- String []args in Java
- Sum-All Quadruples in Java
- ORM Tools in Java
- Odious Number in Java
- Total Decoding Messages in Java
- Check LinkedLists are Equal
- Rat in a Maze Problem in Java
- Sudoku in Java
- finally Keyword in Java
- Find Elected Candidate Problem in Java
- Christmas Tree Pattern in Java
- Double Hashing in Java
- Generate Binary Numbers 1 to n in Java
- Java Program to Implement Heuristic Approach to Solve Set Packing
- Magic Square in Java
- Possible Paths from Top Left to Bottom Right of a Matrix in Java
- Java Program to Recover Binary Search Tree
- LCA in Binary Tree in Java
- Palindrome Partitioning Problem in Java
- Rehashing in Java
- Difference Between ConcurrentHashMap, HashTable, and Synchronized Map in Java
- Difference Between JDBC and Hibernate in Java
- Round Robin Scheduling Program in Java
- Types of Statements in Java
- Default Constructor in Java
- Diameter of a Binary Tree in Java
- Compound Assignment Operator in Java
- Prime Points in Java
- Tie Breaker Problem in Java
- What is Java Programming Used For
- Butterfly Pattern in Java
- Fish Pattern in Java
- Convert Binary Tree to Doubly Linked List (DLL) Java
- Getting Synchronized Map from Java TreeMap
- Flag Pattern in Java
- Kite pattern in Java
- Java append() Method
- Java Array.asList() Method
- Swastika Pattern in Java
- Tug of War in Java
- Java Record
- Letter Combination of a Phone Number in Java
- Clone HashMap in Java
- Fibodiv Number in Java
- Minimum Vertical Sum Problem in Java
- StringBuffer Class in Java
- Heart Pattern in Java
- How to check data type in Java
- Text Justification in Java
- Java Array Clone
- Use of final Keyword in Java
- Factorial of a Large Number in Java
- Race Condition in Java
- Static Array in Java
- Water Jug Problem in Java
- Electricity Bill Program in Java
- Facts about null in Java
- Maximizing Profit in Stock Buy Sell in Java
- Permutation Coefficient in Java
- Convert List to String in Java
- List of Constants in Java
- MOOD Factors to Assess a Java Program
- Computing Digit Sum of All Numbers From 1 to n in Java
- Read PDF File in Java
- Finding Odd Occurrence of a Number in Java
- Java Indentation
- Zig Zag Star and Number Pattern in Java
- Check Whether a Number is a Power of 4 or not in Java
- Kth Smallest in an Unsorted Array in Java
- BlockingQueue in Java
- Next Greater Element in Java
- Star Numbers in Java
- 3N+1 Problem in Java
- Java Program to Find Local Minima in An Array
- Processing Speech in Java
- Java Output Formatting
- House Numbers in Java
- Java Program to Generate Binary Numbers
- Longest Odd-Even Subsequence in Java
- Java Subtract Days from Current Date
- Java Future Example
- Minimum Cost Path Problem in Java
- Diffie-Hellman Algorithm in Java
- Ganesha's Pattern in Java
- Hamming Code in Java
- Map of Map in Java
- Print Pencil Shape Pattern in Java
- Zebra Puzzle in Java
- Display Unique Rows in a Binary Matrix in Java
- Rotate A Matrix By 180 Degree in Java
- Dangling Else Problem in Java
- Dutch National Flag Problem in Java
- Java Calculate Average of List
- compareToIgnoreCase Java
- Trimorphic Numbers in Java
- Arithmetic Exception in Java
- Java instanceof operator
- Java Localization
- Minimum XOR Value Pair in Java
- Iccanobif Numbers in Java
- Java Program to Count the Occurrences of Each Character
- Java Technologies List
- Java Program to Find the Minimum Number of Platforms Required for a Railway Station
- Shift Operators in Java
- Final Object in Java
- Java OCR
- Object Definition in Java
- Shadowing in Java
- Zipping and Unzipping Files in Java
- Display the Odd Levels Nodes of a Binary Tree in Java
- Java Variable Declaration
- Nude Numbers in Java
- Java Programming Challenges
- Java URL Encoder
- anyMatch() in Java 8
- Sealed Class in Java
- Camel case in Java
- Career Options for Java Developers to Aim in 2022
- Java Progress Bar
- Maximum Rectangular Area in a Histogram in Java
- Polygonal Number in Java
- Two Sorted LinkedList Intersection in Java
- Set Matrix Zeros in Java
- Find Number of Island in Java
- Balanced Prime Number in Java
- Minecraft Bedrock vs Java Minecraft
- arr.length vs arr[0].length vs arr[1].length in Java
- Future in Java 8
- How to Set Timer in Java
- Construct the Largest Number from the Given Array in Java
- Java SHA
- Minimum Coins for Making a Given Value in Java
- Eclipse Shortcuts Java
- Empty Statement in Java
- Java Program to Implement Two Stacks in an Array
- Java Snippet
- Longest Arithmetic Progression Sequence in Java
- Types of Sockets in Java
- Java Program to Add Digits Until the Number Becomes a Single Digit Number
- Next Greater Number with Same Set of Digits in Java
- Split the Number String into Primes in Java
- Java Cron Expression
- Huffman Coding Java
- Java Snippet Class
- Why Java is So Popular
- Java Project idea
- Java Web Development
- Brilliant Numbers in Java
- Sort Elements by Frequency in Java
- Beautiful Array in Java
- Moran Numbers in Java
- Intersection Point of Two Linked List in Java
- Sparse Number in Java
- How to Check JRE Version
- Java Programming Certification
- Two Decimal Places Java
- Eclipse Change Theme
- Java how to Convert Bytes to Hex
- Decagonal Numbers in Java
- Java Binary to Hexadecimal Conversion
- Java Hexadecimal to Binary Conversion
- How to Capitalize the First Letter of a String in Java
- Java &0XFF Example
- Stream findFirst() Method in Java
- Balanced Parentheses in Java
- Caesar Cipher Program in Java
- next() vs nextLine()
- Java Split String by Comma
- Spliterator in java 8
- Tree Model Nodes in Jackson
- Types of events in Java
- Callable and Future in Java
- How to Check Current JDK Version installed in Your System Using CMD
- How to Round Double and Float up to Two Decimal Places in Java
- Java 8 Multimap
- Parallel Stream in Java
- Java Convert Bytes to Unsigned Bytes
- Java SFTP
- Display List of TimeZone with GMT and UTC in Java
- Binary Strings Without Consecutive Ones in Java
- Convert IP to Binary in Java
- Java Macro
- Returning Multiple Values in Java
- Centered Square Numbers in Java
- ProcessBuilder in Java
- How to Clear Java Cache
- IntSummaryStatistics Class in Java
- Java ProcessBuilder Example
- Java Program to Delete a Directory
- Java Program to Print Even Odd Using Two Threads
- Java Variant
- MessageDigest in Java
- Alphabet Pattern in Java
- Java Linter
- Java Mod Example
- Stone Game in Java
- TypeErasure in Java
- How to Remove substring from String in Java
- Program to print a string in vertical in Java
- How to Split a String between Numbers and Letters
- String Handling in Java
- Isomorphic String in Java
- Java ImageIO Class
- Minimum Difference Subarrays in Java
- Plus One to Array Problem in Java
- Unequal Adjacent Elements in Java
- Java Parallel Stream Example
- SHA Hashing in Java
- How to make Java projects
- Java Fibers
- Java MD5 Hashing Example
- Hogben Numbers in Java
- Self-Descriptive Numbers in Java
- Hybrid Inheritance in Java
- Java IP Address (IPv4) Regex Examples
- Converting Long to Date in JAVA
- GCD of Different SubSequences in Java
- Sylvester Sequence in Java
- Console in Java
- Asynchronous Call in Java
- Minimum Window Substring in Java
- Nth Term of Geometric Progression in Java
- Coding Guidelines in Java
- Couple Holding Hands Problem in Java
- Count Ones in a Sorted binary array in Java
- Ordered Pair in Java
- Tetris Game in Java
- Factorial Trailing Zeroes in Java
- Java Assert Examples
- Minimum Insertion To Form A Palindrome in Java
- Wiggle Sort in Java
- Java DOM
- Java Exit Code 13
- Java JFileChooser
- What is LINQ
- NZEC in Java
- Box Stacking Problem
- K Most Frequent Elements in Java
- Parallel Programming in Java
- How to Generate JVM Heap Memory Dump
- Java Program to use Finally Block for Catching Exceptions
- Count Login Attempts Java
- Largest Independent Set in Java
- Longest Subarray With All Even or Odd Elements in Java
- Open and Closed Hashing in Java
- DAO Class in Java
- Kynea Numbers in Java
- UTF in Java
- Zygodromes in Java
- ElasticSearch Java API
- Form Feed in Java
- Java Clone Examples
- Payment Gateway Integration in Java
- What is PMD
- RegionMatches() Method in Java
- Repaint() Method in Java
- Serial Communication in Java
- Count Double Increasing Series in A Range in Java
- Longest Consecutive Subsequence in Java
- Smallest Subarray With K Distinct Numbers in Java
- String Sort Custom in Java
- Count Number of Distinct Substrings in a String in Java
- Display All Subsets of An Integer Array in Java
- Digit Count in a Factorial Of a Number in Java
- Valid Parentheses Problem in Java
- DAO Class in Java
- Median Of Stream Of Running Integers in Java
- Arrow Operator in Java
- Java Learning app
- Create Preorder Using Postorder and Leaf Nodes Array
- Display Leaf nodes from Preorder of a BST in Java
- Unicodes for Operators in Java
- XOR and XNOR operators in Java
- AWS Lambda in Java
- AWS Polly in Java
- SAML in Java
- SonarQube in Java
- UniRest in Java
- Override equals method in Java
- Undo and Redo Operations in Java
- Size of longest Divisible Subset in an Array in Java
- Sort An Array According To The Set Bits Count in Java
- Two constructors in one class in Java
- Union in Java
- What is New in Java 15
- ART in Java
- Definite Assignment in Java
- Cast Operator in Java
- Diamond operator in Java
- Java Singleton Enum
- Size of longest Divisible Subset in an Array in Java
- Three-way operator | Ternary operator in Java
- GoF Design Pattern Java
- Java Programming Certification
- Shorthand Operator in Java
- What is new in Java 17
- How to Find the Java Version in Linux
- What is New in Java 12
- Exception in Thread Main java.util.NoSuchElementException no line Found
- How to reverse a string using recursion in Java
- Java Program to Reverse a String Using Stack
- Java Program to Reverse a String Using the Stack Data Structure
- Reverse Middle Words of a String in Java
- Sastry Numbers in Java
- Sum of LCM in Java
- Tilde Operator in Java
- 8 Puzzle problems in Java
- Maximum Sum Such That No Two Elements Are Adjacent in Java
- Reverse a String in Place in Java
- Reverse a string Using a Byte array in Java
- Reverse a String Using Java Collections
- Reverse String with Special Characters in Java
- get timestamp in java
- How to convert file to hex in java
- AbstractSet in java
- List vs Set vs Map in Java
- Birthday Problem in Java
- How to Calculate the Time Difference Between Two Dates in Java
- Number of Mismatching Bits in Java
- Palindrome Permutation of a String in Java
- Grepcode java.util.Date
- How to add 24 hrs to date in Java
- How to Change the Day in The Date Using Java
- Java ByteBuffer Size
- java.lang.NoSuchMethodError
- Maximum XOR Value in Java
- How to Add Hours to The Date Object in Java
- How to Increment and Decrement Date Using Java
- Multithreading Scenarios in Java
- Switch case with enum in Java
- Longest Harmonious Subsequence in Java
- Count OR Pairs in Java
- Merge Two Sorted Arrays Without Extra Space in Java
- How to call a concrete method of abstract class in Java
- How to create an instance of abstract class in Java
- Java Console Error
- 503 error handling retry code snippets Java
- Implementation Of Abstraction In Java
- How to avoid thread deadlock in Java
- Number of Squareful Arrays in Java
- One-Time Password Generator Code In Java
- Real-Time Face Recognition In Java
- Converting Integer Data Type to Byte Data Type Using Typecasting in Java
- How to Generate File checksum Value
- Index Mapping (or Trivial Hashing) With Negatives allowed in Java
- Shortest Path in a Binary Maze in Java
- customized exception in Java
- How to solve deprecated error in Java
- CloneNotSupportedException in Java with Examples
- Difference Between Function and Method in Java
- Immutable List in Java
- Nesting Of Methods in Java
- How to Convert Date into Character Month and Year Java
- How to Mock Lambda Expression in Java
- How to Return Value from Lambda Expression Java
- if Condition in Lambda Expression Java
- Chained Exceptions in Java
- Final static variable in Java
- Java File Watcher
- Various Operations on HashSet in Java
- Word Ladder Problem in Java
- Various Operations on Queue in Java
- Various Operations on Queue Using Linked List in Java
- Various Operations on Queue Using Stack in Java
- Get Yesterday's Date from Localdate Java
- Get Yesterday's Date by No of Days in Java
- Advantages of Lambda Expression in Java 8
- Cast Generic Type to Specific type Java
- ConcurrentSkipListSet in Java
- Fail Fast Vs. Fail-Safe in Java
- Get Yesterday's Date in Milliseconds Java
- Get Yesterday's Date Using Date Class Java
- Getting First Date of Month in Java
- Gregorian Calendar Java Current Date
- How to Calculate Time Difference Between Two Dates in Java
- How to Calculate Week Number from Current Date in Java
- Keystore vs Truststore
- Leap Year Program in Java
- Online Java Compiler GDB
- Operators in Java MCQ
- Separators In Java
- StringIndexOutOfBoundsException in Java
- Anonymous Function in Java
- Default Parameter in Java
- Group by Date Code in Java
- How to add 6 months to Current Date in Java
- How to Reverse A String in Java Letter by Letter
- Java 8 Object Null Check
- synchronized Keyword in Java
- Arithmetic Operators in Java
- Types of JDBC Drivers in Java
- Unmarshalling in Java
- Write a Program to Print Reverse of a Vowels String in Java
- ClassNotFound Exception in Java
- Null Pointer Exception in Java
- Why Does BufferedReader Throw IOException in Java
- Java Program to Add two Complex Numbers
- Right Shift Zero Fill Operator in Java
- Static Block in Java
- Accessor and Mutator in Java
- Array of Class Objects in Java
- Benefits of Generics in Java
- Can Abstract Classes Have Static Methods in Java
- ClassNotFoundException Java
- Creating a Custom Generic Class in Java
- Generic Queue Java
- Getting Total Hours From 2 Dates in Java
- How to add 2 dates in Java
- How to Break a Date and Time in Java
- How to Call Generic Method in Java
- How to Increment and Decrement Date using Java
- Java Class Methods List
- Java Full Stack Developer
- Java.lang.NullPointerException
- Least Operator to Express Number in Java
- Shunting Yard Algorithm in Java
- Singleton Class in Java
- Switch Case Java
- Treeset Java Operations
- Logical Operators in Java
- What is Cast Operator in Java
- What is Jersey in Java
- Alternative to Java Serialization
- API Development in Java
- Disadvantage of Multithreading in Java
- Find the row with the maximum number of 1s
- Generic Comparator in Java
- Generic LinkedList in Java
- Generic Programming in Java Example
- How Can I Give the Default Date in The Array Java
- How to Accept Date in Java
- How to add 4 years to Date in Java
- How to Check Date Equality in Java
- How to Modify HTML File Using Java
- Java 8 Multithreading Features
- Java Abstract Class and Methods
- Java Thread Dump Analyser
- Process vs. Thread in Java
- Reverse String Using Array in Java
- Assignment Operators in Java
- Bitwise Operators in Java
- Union and Intersection Of Two Sorted Arrays In Java
- Vector Operations Java
- Java Books Multithreading
- Advantages of Generics in Java
- Generic Code in Java
- Generic Method in Java Example
- Getting a Range of Dates in Java
- Getting the Day from a Date in Java
- How Counter Work with Date Using Java
- How to Add Date in Arraylist Java
- How to Create a Generic List in Java
- Java Extend Multiple Classes
- Java Function
- Java Generics Design Patterns
- Why Are Generics Used in Java
- XOR Binary Operator in Java
- Check if the given string contains all the digits in Java
- Constructor in Abstract Class in Java
- Count number of a class objects created in Java
- Difference Between Byte Code and Machine Code in Java
- Java Program to Append a String in an Existing File
- Main thread in Java
- Store Two Numbers in One Byte Using Bit Manipulation in Java
- The Knight's Tour Problem in Java
- Business Board Problem in Java
- Business Consumer Problem in Java
- Buy as Much Candles as Possible Java Problem
- Get Year from Date in Java
- How to Assign Static Value to Date in Java
- Java List Node
- Java List Sort Lambda
- Java Program to Get the Size of a Directory
- Misc Operators in Java
- Reverse A String and Reverse Every Alternative String in Java
- Reverse a String in Java Using StringBuilder
- Reverse Alternate Words in A String Java
- Size of Empty Class in Java
- Titniry Operation in Java
- Triple Shift Operator in Java
- Conditional Operators in Java
- View Operation in Java
- What is Linked list Operation in Java
- What is Short Circuit && And or Operator in Java
- What is the & Operator in Java
- Why to use enum in Java
- XOR Bitwise Operator in Java
- XOR Logical Operator Java
- Convert JSON to Java Object Online
- Difference between comparing String using == and .equals() method in Java
- Difference Between Singleton Pattern and Static Class in Java
- Difference Between Static and Non-Static Nested Class in Java
- Getting Date from Calendar in Java
- How to Swap or Exchange Objects in Java
- Java Get Class of Generic Parameter
- Java Interface Generic Parameter
- Java Map Generic
- Java NLP
- Java Number Class
- Java Program for Maximum Product Subarray
- Java Program To Print Even Length Words in a String
- Logger Class in Java
- Manacher's Algorithm in Java
- Mutable Class in Java
- Online Java IDE
- Package getImplementationVersion() method in Java with Examples
- Set Default Close Operation in Java
- Sorting a Java Vector in Descending Order Using Comparator
- Types of Interfaces in Java
- Understanding String Comparison Operator in Java
- User-Defined Packages in Java
- Valid variants of main() in Java
- What is a Reference Variable in Java
- What is an Instance in Java
- What is Retrieval Operation in ArrayList Java
- When to Use the Static Method in Java
- XOR Operations in Java
- Array Declaration in Java
- Bad Operand Types Error in Java
- Data Structures in Java
- Generic Type Casting In Java
- Multiple Inheritance in Java
- Nested Initialization for Singleton Class in Java
- Object in Java
- Recursive Constructor Invocation in Java
- Java Language / What is Java
- Why is Java Platform Independent
- Card Flipping Game in Java
- Create Generic Method in Java
- Difference between super and super() in Java with Examples
- for loop enum Java
- How to Convert a String to Enum in Java
- Illustrate Class Loading and Static Blocks in Java Inheritance
- Introduction to Java
- Java Lambda foreach
- Java Latest Version
- Java Method Signature
- Java Practice Programs
- Java SwingWorker Class
- java.util.concurrent.RecursiveAction class in Java With Examples
- Largest Palindrome by Changing at Most K-digits in Java
- Parameter Passing Techniques in Java with Examples
- Reverse a String in Java Using a While Loop
- Reverse a String Using a For Loop in Java
- Short-Circuit Operator in Java
- Java 8 Stream API
- XOR Operation on Integers in Java
- XOR Operation on Long in Java
- Concrete Class in Java
- Difference between Character Stream and Byte Stream in Java
- Difference Between Static and Non-Static in Java
- Different Ways to Convert java.util.Date to java.time.LocalDate in Java
- Find the Good Matrix Problem in Java
- How Streams Work in Java
- How to Accept Different Formats of Date in Java
- How to Add Date in MySQL from Java
- How to Find the Size of int in Java
- How to Make a Field Serializable in Java
- How to Pass an Array to Function in Java
- How to Pass an ArrayList to a Method in Java
- Implementing the Java Queue Interface
- Initialization of local variable in a conditional block in Java
- isnull() Method in Java
- Java Array Generic
- Java Program to Demonstrate the Lazy Initialization Non-Thread-Safe
- Java Program to Demonstrate the Non-Lazy Initialization Thread-Safe
- Java Static Field Initialization
- Machine Learning Using Java
- Mars Rover Problem in Java
- Model Class in Java
- Nested Exception Handling in Java
- Program to Convert List to Stream in Java
- Static Polymorphism in Java
- Static Reference Variables in Java
- Sum of Two Arrays in Java
- What is Is-A-Relationship in Java
- When to Use Vector in Java
- Which Class cannot be subclassed in Java
- Word Search Problem in Java
- XOR Operation Between Sets in Java
- Burger Problem in Java Game
- Convert Set to List in Java
- Floyd Triangle in Java
- How to Call Static Blocks in Java
- Interface Attributes in Java
- Java Applications in the Real World
- Java Concurrent Array
- Java Detect Date Format
- Java Interface Without Methods
- Java Iterator Performance
- Java Packet
- Java Static Instance of Class
- Java TreeMap Sort by Value
- Length of List in Java
- List of Checked Exceptions in Java
- Message Passing in Java
- Product Maximization Problem in Java
- Terminal Operations in Java 8
- Understanding Base Class in Java
- Difference between Early Binding and Late Binding in Java
- Collectors toCollection() in Java
- Difference between ExecutorService execute() and submit() method in Java
- Difference between Java and Core Java
- Different Types of Recursions in Java
- Initialize a static map in Java with Examples
- Java API
- Merge Sort Using Multithreading in Java
- Why Thread.stop(), Thread.suspend(), and Thread.resume() Methods are Deprecated After JDK 1.1 Version
- Circular Primes in Java
- Difference Between poll() and remove() Method of a Queue
- EvalEx Java: Expression Evaluation in Java
- Exeter Caption Contest Java Program
- FileInputStream finalize() Method in Java
- Find the Losers of the Circular Game problem in Java
- Finding the Differences Between Two Lists in Java
- Finding the Maximum Points on a Line in Java
- Get Local IP Address in Java
- Handling "Handler dispatch failed" Nested Exception: java.lang.StackOverflowError in Java
- Harmonic Number in Java
- How to Find the Percentage of Uppercase Letters, Lowercase Letters, Digits, and Special Characters in a String Using Java
- Interface Variables in Java
- Java 8 Interface Features
- Java Class Notation
- Java Exception Messages Examples and Explanations
- Java Package Annotation
- Java Program to Find First Non-Repeating Character in String
- Java Static Type Vs Dynamic Type
- Kaprekar Number in Java
- Multitasking in Java
- Niven Number in Java
- Rhombus Pattern in Java
- Shuffle an Array in Java
- Static Object in Java
- The Scope of Variables in Java
- Toggle String in Java
- Use of Singleton Class in Java
- What is the Difference Between Future and Callable Interfaces in Java
- Aggregate Operation in Java 8
- Bounded Types in Java
- Calculating Batting Average in Java
- Compare Two LinkedList in Java
- Comparison of Autoboxed Integer objects in Java
- Count Tokens in Java
- Cyclomatic Complexity in Java
- Deprecated Meaning in Java
- Double Brace Initialization in Java
- How to prevent objects of a class from Garbage Collection in Java
- Java Cast Object to Class
- Java isAlive() Method
- Java Line Feed Character
- Java Program for Maximum Product Subarray
- java.net.MulticastSocket class in Java
- Keytool Error java.io.FileNotFoundException
- Matrix Diagonal Sum in Java
- Number of Boomerangs Problem in Java
- Sieve of Eratosthenes Algorithm in Java
- Similarities Between Bastar and Java
- Spring vs. Struts in Java
- Switch Case in Java 12
- The Pig Game in Java
- Unreachable Code Error in Java
- Who Were the Kalangs of Java
- 2048 Game in Java
- Abundant Number in Java
- Alpha-Beta Pruning Java
- ArgoUML Reverse Engineering Java
- Can Constructor be Static in Java
- Can we create object of interface in Java
- Chatbot Application in Java
- Difference Between Component and Container in Java
- Difference Between Java.sql and Javax.sql
- Find A Pair with Maximum Product in Array of Integers
- Goal Stack Planning Program in Java
- Half Diamond Pattern in Java
- How to find trigonometric values of an angle in Java
- How to Override tostring() method in Java
- Inserting a Node in a Doubly Linked List in Java
- Java 9 Immutable Collections
- Java 9 Interface Private Methods
- Java Convert Array to Collection
- Java Transaction API
- Methods to Take Input in Java
- Parallelogram Pattern in Java
- Power of a Number in Java
- Reminder Program in Java
- Sliding Window Protocol in Java
- Static Method in Java
- String Reverse in Java 8 Using Lambdas
- Types of Threads in Java
- What is thread safety in Java? How do you achieve it?
- xxwxx.dll Virus Java 9
- Java 8 Merge Two Maps with Same Keys
- Java 8 StringJoiner, String.join(), and Collectors.joining()
- Java 9 @SafeVarargs Annotation Changes
- Java 9 Stream API Improvements
- Java 11 var in Lambda Expressions
- Sequential Search Java
- Thread Group in Java
- User Thread Vs. Daemon Thread in Java
- Collections Vs. Streams in Java
- F in Java
- Import statement in Java
- init() Method in Java
- Java Generics Jenkov
- Ambiguity in Java
- Benefits of Learning Java
- Designing a Vending Machine in Java
- Monolithic Applications in Java
- Name Two Types of Java Program
- Random Access Interface in Java
- Rust Vs. Java
- Types of Constants in Java
- Execute the Main Method Multiple Times in Java
- Find the element at specified index in a Spiral Matrix in Java
- Find The Index of An Array Element in Java
- Mark-and-Sweep Garbage Collection Algorithm in Java
- Shadowing of Static Functions in Java
- Straight Line Numbers in Java
- Zumkeller Numbers in Java
- Virtual Threads in Java 21
- Add Two Numbers Without Using Operator in Java
- Automatic Type Promotion in Java
- ContentPane Java
- Difference Between findElement() and findElements() in Java
- Difference Between Inheritance and Interfaces in Java
- Difference Between Jdeps and Jdeprscan tools in Java
- Find Length of String in Java Without Using Function
- InvocationTargetException in Java
- Java Maps to JSON
- Key Encapsulation Mechanism API in Java 21
- Placeholder Java
- String Templates in Java 21
- Why Java is Robust Language
- Collecting in Java 8
- containsIgnoreCase() Method in Java
- Convert String to Biginteger In Java
- Convert String to Map in Java
- Define Macro in Java
- Difference Between Lock and Monitor in Java Concurrency
- Difference Between the start() and run() Methods in Java
- Generalization and Specialization in Java
- getChannel() Method in Java
- How to Check Whether an Integer Exists in a Range with Java
- HttpEntity in Java
- Lock Framework Vs. Thread Synchronization in Java
- Niven Number Program in Java
- Passing Object to Method in Java
- Pattern Matching for Switch in Java 21
- Swap First and Last Digit of a Number in Java
- Adapter Design Pattern in Java
- Best Automation Frameworks for Java
- Building a Search Engine in Java
- Bytecode Verifier in Java
- Caching Mechanism in Java
- Comparing Two HashMap in Java
- Cryptosystem Project in Java
- Farthest from Zero Program in Java
- How to Clear Linked List in Java
- Primitive Data Type Vs. Object Data Type in Java
- setBounds() Method in Java
- Unreachable Code or Statement in Java
- What is Architecture Neutral in Java
- Difference between wait and notify in Java
- Dyck Path in Java
- Find the last two digits of the Factorial of a given Number in Java
- How to Get an Environment Variable in Java
- Java Program to open the command prompt and insert commands
- JVM Shutdown Hook in Java
- Semiprimes Numbers in Java
- 12 Tips to Improve Java Code Performance
- Ad-hoc Polymorphism in Java
- Array to String Conversion in Java
- CloudWatch API in Java
- Essentials of Java Programming Language
- Extends Vs. Implements in Java
- 2d Array Sorting in Java
- Aliquot Sequence in Java
- Authentication and Authorization in Java
- Cannot Find Symbol Error in Java
- Compare Two Excel Files in Java
- Consecutive Prime Sum Program in Java
- Count distinct XOR values among pairs using numbers in range 1 to N
- Difference Between Two Tier and Three Tier Architecture in Java
- Different Ways of Reading a Text File in Java
- Empty Array in Java
- FCFS Program in Java with Arrival Time
- Immutable Map in Java
- K-4 City Program in Java
- Kahn's algorithm for Topological Sorting in Java
- Most Popular Java Backend Tools
- Recursive Binary Search in Java
- Set Intersection in Java
- String Reverse Preserving White Spaces in Java
- The Deprecated Annotation in Java
- What is JNDI in Java
- Backtracking in Java
- Comparing Doubles in Java
- Consecutive Prime Sum in Java
- Finding Missing Numbers in an Array Using Java
- Good Number Program in Java
- How to Compress Image in Java Source Code
- How to Download a File from a URL in Java
- Passing an Object to The Method in Java
- Permutation program in Java
- Profile Annotation in Java
- Scenario Based Questions in Java
- Understanding Static Synchronization in Java
- Types of Errors in Java
- Abstract Factory Design Pattern in Java
- Advantages of Kotlin Over Java
- Advantages of Methods in Java
- Atomic Boolean in Java
- Bitset Class in Java
- Bouncy Castle Java
- Chained Exception in Java
- Colossal Numbers in Java
- Compact Profiles Java 8
- Convert Byte to Image in Java
- Convert Set to Array in Java
- Copy ArrayList to another ArrayList Java
- Copy Data from One File to Another in Java
- Dead Code in Java
- Driver Class Java
- EnumMap in Java
- Farthest Distance of a 0 From the Centre of a 2-D Matrix in Java
- How to Terminate a Program in Java
- Instance Block in Java
- Iterative Constructs in Java
- Java 10 var Keyword
- Java Games
- Nested ArrayList in Java
- Square Pattern in Java
- String Interpolation in Java
- Unnamed Classes and Instance Main Method in Java 21
- What is difference between cacerts and Keystore in Java
- Agile Principles Patterns and Practices in Java
- Color Method in Java
- Concurrent Collections in Java
- Create JSON Node in Java
- Difference Between Checkbox and Radio Button in Java
- Difference Between Jdeps and Jdeprscan Tools in Java
- Difference Between Static and Dynamic Dispatch in Java
- Difference Between Static and Non-Static Members in Java
- Error Java Invalid Target Release 9
- Filedialog Java
- String Permutation in Java
- Structured Concurrency in Java
- Uncaught Exception in Java
- ValueOf() Method in Java
- Virtual Thread in Java
- Difference Between Constructor Overloading and Method Overloading in Java
- Difference Between for loop and for-each Loop in Java
- Difference Between Fork/Join Framework and ExecutorService in Java
- Difference Between Local, Instance, and Static Variables in Java
- Difference Between Multithreading and Multiprocessing in Java
- Difference Between Serialization and Deserialization in Java
- Difference Between Socket and Server Socket in Java
- Advantages of Immutable Classes in Java
- BMI Calculator Java
- Code Coverage Tools in Java
- How to Declare an Empty Array in Java
- How To Resolve Java.lang.ExceptionInInitializerError in Java
- Java 18 Snippet Tag with Example
- Object Life Cycle in Java
- print() Vs. println() in Java
- @SuppressWarnings Annotation in Java
- Types of Cloning in Java
- What is portable in Java
- What is the use of an interpreter in Java
- Abstract Syntax Tree (AST) in Java
- Aliasing in Java
- CRUD Operations in Java
- Euclid-Mullin Sequence in Java
- Frame Class in Java
- Initializing a List in Java
- Number Guessing Game in Java
- Number of digits in N factorial to the power N in Java
- Rencontres Number in Java
- Skewed Binary Tree in Java
- Vertical zig-zag traversal of a tree in Java
- Wap to Reverse a String in Java using Lambda Expression
- Concept of Stream in Java
- Constraints in Java
- Context Switching in Java
- Dart Vs. Java
- Dependency Inversion Principle in Java
- Difference Between Containers and Components in Java
- Difference Between CyclicBarrier and CountDownLatch in Java
- Difference Between Shallow and Deep Cloning in Java
- Dots and Boxes Game Java Source code
- DRY Principle Java
- How to get File type in Java
- IllegalArgumentException in Java example
- Is the main() method compulsory in Java
- Java Paradigm
- Lower Bound in Java
- Method Binding in Java
- Overflow and Underflow in Java
- Padding in Java
- Passing and Returning Objects in Java
- Single Responsibility Principle in Java
- ClosedChannelException in Java with Examples
- How to Fix java.net.ConnectException Connection refused connect in Java
- java.io.UnsupportedEncodingException in java with Examples
- Selection Statement in Java
- Difference Between Java 8 and Java 9
- Difference Between Nested Class and Inner Class in Java
- Difference Between OOP and POP in Java
- Difference Between Static and Dynamic in Java
- Difference Between Static Binding and Dynamic Binding in Java
- Difference Between Variable and Constant in Java
- Advantages of Generics in Java
- Alternate Pattern Program in Java
- Architecture Neutral in Java
- AutoCloseable Interface in Java
- BitSet Class in Java
- Border Layout Manager in Java
- Digit Extraction in Java
- Dynamic Variable in Java
- How to Convert Double to string in Java
- How to Convert Meter to Kilometre in Java
- How to Install SSL Certificate in Java
- How to Protect Java Source Code
- How to Use Random Object in Java
- Java Backward Compatibility
- Java New String Class Methods from Java 8 to Java 17
- Mono in Java
- Object to int in Java
- Predefined Streams in Java
- Prime Factor Program in Java
- Transfer Statements in Java
- What is Interceptor in Java
- Java Array Methods
- java.lang.Class class in Java
- Reverse Level Order Traversal in Java
- Working with JAR and Manifest files In Java
- Alphabet Board Path Problem in Java
- Composite Design Pattern Java
- Default and Static Methods in Interface Java 8
- Difference Between Constraints and Annotations in Java
- Difference Between fromJson() and toJson() Methods of GSON in Java
- Difference Between Java 8 and Java 11
- Difference Between map() and flatmap() Method in Java 8
- Difference Between next() and nextLine() Methods in Java
- Difference Between orTimeout() and completeOnTimeOut() Methods in Java 9
- Disadvantages of Array in Java
- How Synchronized works in Java
- How to Create a Table in Java
- ID Card Generator Using Java
- Introspection in JavaBeans
- Java 15 Features
- Java CLOB
- Java Object Model
- Java Tools and Command-List
- Next Permutation Java
- Number Guessing Game in Java
- Object as Parameter in Java
- Optimizing Java Code Performance
- Pervasive Shallowness in Java
- Sequenced Collections in Java 21
- Stdin and Stdout in Java
- Stream count() Function in Java
- String.strip() Method in Java
- Vertical Flip Matrix Problem in Java
- Calling Object in Java
- Characteristics of Constructor in Java
- Counting Problem in Multithreading in Java
- Creating Multiple Pools of Objects of Variable Size in Java
- Default Exception in Java
- How to Install Multiple JDK's in Windows
- Differences Between Vectors and Arrays in Java
- Duplicate Class Errors in Java
- Example of Data Hiding in Java
- Foreign Function and Memory APIs in Java 21
- Generic Tree Implementation in Java
- getSource() Method in Java
- Giuga numbers in Java
- Hessian Java
- How to Connect Login Page to Database in Java
- Difference between BlueJ and JDK 1.3
- How to Solve Incompatible Types Error in Java
- Java 8 Method References
- Java 9 Try with Resources Improvements
- Menu-Driven Program in Java
- Mono Class in Java
- Multithreading Vs. Asynchronous in Java
- Nested HashMap in Java
- Number Series Program in Java
- Object Slicing in Java
- Oracle Java
- Passing and Returning Objects in Java
- Print 1 to 100 Without Loop in Java
- Remove elements from a List that satisfy given predicate in Java
- Replace Element in Arraylist Java
- Sliding Puzzle Game in Java
- Strobogrammatic Number in Java
- Web Methods in Java
- Web Scraping Java
- Window Event in Java
- @Builder Annotation in Java
- Advantages of Abstraction in Java
- Advantages of Packages in Java
- Bounce Tales Java Game Download
- Breaking Singleton Class Pattern in Java
- Building a Brick Breaker Game in Java
- Building a Scientific Calculator in Java
- Circle Program in Java
- Class Memory in Java
- Convert Byte to an Image in Java
- Count Paths in Given Matrix in Java
- Difference Between Iterator and ListIterator in Java with Example
- Distinct Character Count Java Stream
- EOFException in Java
- ExecutionException Java 8
- Generic Object in Java
- How to Create an Unmodifiable List in Java
- How to Create Dynamic SQL Query in Java
- How to Return a 2D Array in Java
- Java 8 Stream.distinct() Method
- Java setPriority() Method
- Mutator Methods in Java
- Predicate Consumer Supplier Java 8
- Program to Generate CAPTCHA and Verify User Using Java
- Random Flip Matrix in Java
- System Class in Java
- Types of Errors in Java
- Vigenere Cipher Program in Java
- Behavior-Driven Development (BDD) in Java
- CI/ CD Tools for Java
- cint in Java
- Command Pattern in Java
- CSV to List Java
- Difference Between Java Servlets and CGI
- Difference Between Multithreading Multitasking, and Multiprocessing in Java
- Encoding Three Strings in Java
- How to Import Jar File in Eclipse
- Meta Class Vs. Class in Java
- Meta Class Vs. Super Class in Java
- Print Odd and Even Numbers by Two Threads in Java
- Scoped value in Java
- Upper-Bounded Wildcards in Java
- Wildcards in Java
- Zero Matrix Problem in Java
- All Possible Combinations of a String in Java
- Atomic Reference in Java
- Final Method Overloading in Java| Can We Overload Final Methods
- Constructor in Inheritance in Java
- Design Your Custom Connection Pool in Java
- How Microservices Communicate with Each Other in Java
- How to Convert String to Timestamp in Java
- Java 10 Collectors Methods
- Java and Apache OpenNLP
- Java Deep Learning
- Java Iterator Vs. Listiterator Vs. Spliterator
- Pure Functions in Java
- Use of Constructor in Java | Purpose of Constructor in Java
- Implement Quintet Class with Quartet Class in Java using JavaTuples
- Java Best Practices
- Efficiently Reading Input For Competitive Programming using Java 8
- Length of the longest substring without repeating characters in Java
- Advantages of Inner Class in Java
- AES GCM Encryption Java
- Array Default Values in Java
- Copy File in Java from one Location to Another
- Creating Templates in Java
- Different Packages in Java
- How to Add Elements to an Arraylist in Java Dynamically
- How to Add Splash Screen in Java
- How to Calculate Average Star Rating in Java
- Immutable Class with Mutable Object in Java
- Java instanceOf() Generics
- Set Precision in Java
- Snake Game in Java
- Tower of Hanoi Program in Java
- Two Types of Streams Offered by Java
- Uses of Collections in Java
- Additive Numbers in Java
- Association Vs. Aggregation Vs. Composition in Java
- Covariant and Contravariant Java
- Creating Immutable Custom Classes in Java
- mapToInt() in Java
- Methods of Gson in Java
- Server Socket in Java
- Check String Are Permutation of Each Other in Java
- Containerization in Java
- Difference Between Multithreading and Multiprogramming in Java
- Flyweight Design Pattern
- HMAC Encryption in Java
- How to Clear Error in Java Program
- Strobogrammatic Number in Java
- 5 Types of Java
- Design a Job Scheduler in Java
- Elements of Java Programming
- Generational ZCG in Java 21
- How to Print Arraylist Without Brackets Java
- How to Solve Incompatible Types Error in Java
- Interface Vs. Abstract Class After Java 8
- Java 9 Optional Class Improvements
- Number of GP sequence Problem in Java
- Pattern Matching for Switch
- Range Addition Problem in Java
- Swap Corner Words and Reverse Middle Characters in Java
- Kadane's Algorithm in Java
- Capture the Pawns Problem in Java
- Compact Profiles Java 8
- Find Pair With Smallest Difference in Java
- How to pad a String in Java
- When to use Serialization and Externalizable Interface
- Which Component is responsible to run Java Program
- Difference Between Java and Bastar
- Difference Between Static and Instance Methods in Java
- Difference Between While and Do While loop in Java
- Future Interface in Java
- Invert a Binary tree in Java
- Java Template Engine
- KeyValue Class in JavaTuples
- Quantifiers in Java
- Swapping Pairs of Characters in a String in Java
- Version Enhancements in Exception Handling introduced in Java SE 7
- Find all Palindromic Sub-Strings of a given String in Java
- Find if String is K-Palindrome or not in Java
- Count Pairs from an Array with Even Product of Count of Distinct Prime Factor in Java
- Find if an Array of Strings can be Chained to form a Circle in Java
- Find largest factor of N such that NF is less than K in Java
- Lexicographically First Palindromic String in Java
- LinkedTransferQueue removeAll() method in Java with Examples
- Next Smallest Palindrome problem in Java
- Why Java is not a Purely Object-Oriented Language
- Count all Distinct Pairs with difference Equal to K in Java
- Count Pairs formed by Distinct Element Sub-Arrays in Java
- Even numbers at even index and odd numbers at odd index in Java
- LinkedTransferQueue retainAll() method in Java with Examples
- LinkedTransferQueue tryTransfer() method in Java with Examples
- Number of Equal Count Substrings in Java
- Check if a given string is Even-Odd Palindrome or not in Java
- Check if given String is Pangram or not in Java
- Convert a List of String to a comma separated String in Java
- Duration minusMinutes(long) method in Java with Examples
- Insert a String into another String in Java
- Java Collections checkedQueue() Method with Examples
- String Literal Vs String Object in Java
- ChoiceFormat applyPattern() method in Java with Examples
- ChoiceFormat format() method in Java with Examples
- ChoiceFormat getFormats() method in Java with Examples
- ChoiceFormat hashCode() method in Java with Examples
- ChoiceFormat parse() method in Java with Examples
- CompositeName get() method in Java with Examples
- Difference Between Package and Interface in Java
- DoubleFunction Interface in Java with Examples
- ThaiBuddhistDate now(Clock) method in Java with Example
- ToIntFunction Interface in Java with Examples
- How to Make Object Serializable in Java
- Java Program to Check if Two Words Are Present in a String
- Java Program to Generate Random Hexadecimal Bytes
- ToIntBiFunction Interface in Java with Examples
- AbstractCollection addAll() Method in Java with Examples
- Checking if Two Words Are Present in a String in Java
- DoubleAdder intValue() method in Java with Examples
- DoubleConsumer Interface in Java with Examples
- Generate Random Numbers Using Middle Square Method in Java
- How to Write Robust Programs with the Help of Loops in Java
- Implementing Sparse Vector in Java
- Java.util.concurrent.Exchanger class with Examples
- Java.util.DoubleSummaryStatistics class with Examples
- Java.util.function.BiPredicate interface in Java with Examples
- Java.util.function.LongPredicate interface in Java with Examples
- LongConsumer Interface in Java with Examples
- Predicate.not() Method in Java with Examples
- ToLongBiFunction Interface in Java with Examples
- 10 Ways to Create a Stream in Java
- ChoiceFormat equals() method in Java with Examples
- How to Check if a String contains only ASCII in Java
- How to set the TLS version in Java
- IntSummaryStatistics getCount() method in Java with Examples
- IntSummaryStatistics getMax() method in Java with Examples
- IntSummaryStatistics getMin() method in Java with Examples
- IntSummaryStatistics getSum() method in Java with Examples
- Java Generics to Code Efficiently in Competitive Programming
- Java Program to Extract Content from a PDF
- Java Program to Print Mirror Upper Star Triangle Pattern
- Java Program to Print Spiral Pattern of Numbers
- Java.util.function.DoubleBinaryOperator interface with Examples
- Java.util.function.DoublePredicate interface in Java with Examples
- Java.util.IntSummaryStatistics class with Examples
- Java.util.LongSummaryStatistics class with Examples
- Parallel vs Sequential Stream in Java
- Restrictions on Generics in Java
- Word Count Using Multithreading in Java
- Can we make the main() thread as daemon in Java
- How to Create a File with a Specific charset in Java
- How to Create a File with a Specific File Attribute in Java
- How to Create a File with a Specific Owner and Group in Java
- How to Create and Manipulate a Memory-Mapped File in Java
- Maximum XOR for Each Query in Java
- Represent KN as The Sum of Exactly N numbers in Java
- Spell Checker in Java
- Arranging Coin Problem in Java
- Beautiful Path Code in Java
- Boolean Evaluation in Java
- How to make non daemon thread as daemon in Java
- Java Program to Convert Boolean to Integer
- Java Program to Represent Linear Equations in Matrix Form
- Null Object Design Pattern Java
- Program for Derivative of a Polynomial
- Program to Emulate N Dice roller in Java
- String Compression Problem in Java
- Divide large number represented as string in Java
- Java tricks for Competitive Programming (for Java 8)
- Largest integers with sum of setbits at most K in Java
- Java default Keyword
- Longest Happy String in Java
- Maximum sum of a Subarray with prime integers in Java
- Minimum Swaps to Arrange a Binary Grid in Java
- Array Partition Problem in Java
- Atomic Vs. Volatile in Java
- Difference Between Java and .Net
- Difference Between Java and JDK
- File Descriptor Class in Java
- File Permissions in Java
- Finalizer Chaining in Java
- Find the N-th Value After K Seconds in Java
- FloatBuffer allocate() method in Java With Examples
- FloatBuffer clear() methods in Java with Examples
- FloatBuffer duplicate() method in Java with Examples
- FloatBuffer equals() method in Java with examples
- FloatBuffer put() methods in Java with Examples
- Horizontal Flip Matrix Problem in Java
- Lifetime of Variables in Java
- Matrix Max Sum Path Problem in Java
- Method and Block Synchronization in Java
- Number Complement Problem in Java
- OffSetDate Time getDayOfMonth() method in Java with examples
- OffsetDateTime format() method in Java with examples
- OffsetDateTime getOffset() method in Java with examples
- Rotate a given Matrix in Java in Java
- Solving Sudoku Using Multithreading in Java
- Spiral Matrix Problem in Java
- Third Maximum Number Problem in Java
- Valid Number Problem in Java
- Valid Square Problem in Java
- Atomic Vs. Synchronized in Java
- Blank Final in Java
- Boggle Search Problem in Java
- Custom Classes in Java
- Difference Between java.sql.Time, java.sql.Timestamp and java.sql.Date in Java
- FloatBuffer mark() methods in Java with Examples
- FloatBuffer rewind() methods in Java with Examples
- Generate Random String of Given Size in Java
- Image Processing in Java: Get and Set Pixels
- Java Integer.valueOf() Method
- Interesting Facts About Null in Java
- Iterator Vs. foreach in Java
- Java Numeric Promotion in Conditional Expression
- Java Quantifiers
- Largest Square Matrix Problem in Java
- Object Reference Equality
- Reflect Array in Java
- Stream mapToDouble() in Java with Examples
- Stream noneMatch() Method in Java with Examples
- Stream skip() Method in Java With Examples
- Sum of Numbers with Units Digit K in Java
- Using _ (underscore) as Variable Name in Java
- AbstractSequentialList clear() method in Java with Example
- AtomicIntegerArray set() method in Java with Examples
- AtomicIntegerArray toString() method in Java with Examples
- AtomicLongArray set() method in Java with Examples
- Can We Extend Final Method in Java
- Check If the Given Two Matrices Are Mirror Images of One Another in Java
- Convert A Mobile Numeric Keypad Sequence to Equivalent Sentence
- Difference Between System.out.print() and System.out.println() Function in Java
- Difference Between System.out.println() and System.err.println() in Java
- Do We Need Forward Declarations in Java
- Few Tricky Programs in Java
- Find Largest Rectangle in Matrix Java
- FloatBuffer flip() methods in Java with Examples
- FloatBuffer get() methods in Java with Examples
- How Does Default Virtual Behavior Differ in C++ and Java
- How to Make Java Regular Expression Case Insensitive in Java
- Image Processing in Java
- Image Processing in Java: Colored Image to Negative Image Conversion
- Implementing our Own Hash Table with Separate Chaining in Java
- Island of Isolation in Java
- Java Community Process
- Java Program to Cyclically Permute the Elements of an Array
- Java Program to Find Two Elements Whose Sum is Closest to Zero
- Java Program to Perform Message Encoding Using Matrix Multiplication
- Maximum Score of a Good Subarray in Java
- new Operator Vs. newInstance() Method in Java
- Package getPackages() method in Java with Examples
- Redirecting System.out.println() Output to a File in Java
- Abstract Syntax Tree (AST) Vs. Parse Tree
- Catching Base and Derived Classes as Exceptions in Java
- Create Java temp File
- DoubleBuffer array() method in Java With Examples
- DoubleBuffer clear() methods in Java with Examples
- DoubleBuffer compact() method in Java With Examples
- DoubleBuffer order() methods in Java with Examples
- Effectively Final Variable in Java with Examples
- Euclidean Algorithm in Java
- Find all Primes to a Given Natural Number Using the Sieve of Eratosthenes Method
- Find Common Prime Divisors in Java
- Find Longest Substring Containing Exactly K-Vowels in Java
- Find the Longest Common Prefix using Word-by-Word Matching in Java
- Find the Longest Substring Consisting of Vowels Using Binary Search in Java
- Find the Longest Substring Having K Distinct Vowels in Java
- Image Processing in Java-Comparison of Two Images
- Image Processing in Java - Creating a Random Pixel Image
- Image Processing in Java-Brightness Enhancement
- Image Processing in Java: Coloured Image to Grayscale Image Conversion
- Image Processing in Java: Converting Colored Images to Red, Green, and Blue Images
- Image Processing in Java-Changing Orientation of an Image
- Image Processing in Java - Contrast Enhancement
- Java Optional Class orElseThrow() Method
- Java Precondition
- Java Program to Find the Minimum Distance Between Array Elements
- Java Program to Find the Smallest Positive Number Missing from an Unsorted Array
- Java Program to Implement Associative Array
- Java Program to Increment All Elements of an Array by One
- Java Program to Maximize Count of Substrings Containing at Least 1 Vowel and 1 Consonant
- Java Program to Merge Two Arrays Without Extra Space
- Java Program to Move All Zeros to the Start of an Array
- Java Program to Print Odd Elements at Even Index
- Java Program to Print Odd Elements at Odd Index
- Minimum Suffix Flips in Java
- Number of Restricted Paths From First to Last Node in Java
- Swapping Two Variables in One Line in Java
- Codility Passing Car Problem in Java
- Cover Manhattan Skyline Using The Minimum Number of Rectangles
- Find the Longest Common Prefix Using Binary Search in Java
- Find the Longest Sequence of Zeros in the Binary Representation of an Integer
- Find the Minimum Shift for the Longest Common Prefix in Java
- Find The Smallest Positive Integer That Does Not Occur in A Given Sequence
- Image Processing in Java- Colored Image to Sepia Image Conversion
- Image Processing in Java - Watermarking an Image
- Java Performance Optimization: Tips and Techniques
- Toeplitz matrix in Java
- What is a Memory-Mapped File in Java
- ASCII
- James Gosling : The Father of Java
- Core Java MCQ
- Swap Two Numbers in Java Using Function
- Compound Statement in Java
- Dynamic Initialization in Java
- GENERAL PURPOSE PROGRAMMING LANGUAGE
- HashSet vs TreeSet
MOOD Factors to Assess a Java Program17 Mar 2025 | 6 min read Application quality is critical to the development of software systems, especially large-scale ones. High quality software would reduce the cost of software maintenance, and it enhances the potential software reuse. In order to measure the software quality more quantitatively and objectively, software metrics (MOOD) give impression to be a powerful and effective methodology that decide a grade to an object-oriented application. So, in this section, we will discuss the mood factors to assess an object-oriented application.  MOOD stands for Matrices for Object Oriented Design. It describes the characteristics of an object-oriented application or program. It is used to evaluate a grade of Java program. MOOD factors include the following six software quality indicators or metrices:
Information Hiding factorsMHF and AHF are measures of the use of the information-hiding concept supported by the encapsulation mechanism. Information hiding should be used to:
Method Hiding Factor (MHF)MHF can be calculates by using the following mathematical formula:  Where, Mh(Ci) = hidden Methods in class Ci Md(Ci) = Mv(Ci) + Mh(Ci): Methods defined in Ci Mv(Ci): visible Methods in class Ci TC: Total number of Classes The visible methods measure the class functionality. Enhancing the overall functionality of the class, reduces the MHF. In order to implement this functionality, a top down approach must be adopted. It means that the class implementation must be a step by step decomposition process so that we can add more and more detail in hidden methods that results in incremented MHF. A very low MHF value denotes implementation of insufficiently abstracted methods. Conversely, a high MHF value denotes very little functionality. Therefore, the MHF values must lies within an interval 2,3, and 4. Attribute Hiding Factors (AHF)AHF can be calculates by using the following mathematical formula:  Where, Ah(Ci) = hidden attributes in class Ci Ad(Ci) = Av(Ci) + Ah(Ci): attributes defined in Ci Av(Ci): visible attributes in class Ci TC: Total number of classes AHF is a measure of the use of the information hiding concept supported by the encapsulation mechanism. Information hiding allows coping with complexity by turning complex components into black boxes. AHF should be used as much as possible. Ideally all attributes would be hidden, thus being only accessed by the corresponding class methods. Very low values of AHF should trigger the designers' attention. In general, as AHF increases, the complexity of the program decreases 2,3, and 4. Inheritance FactorsBoth MIF and AIF are measures of inheritance. This is a mechanism for expressing similarity among classes that allows for the portrayal of generalization and specialization relations, and a simplification of the definition of inheriting classes by means of reuse [2,3,4,5]. Method Inheritance Factor (MIF)MIF can be calculated by using the following mathematical formula:  Where, Mi: inherited methods Ma(Ci) = Md(Ci) + Mi(Ci): attributes defined in Ci Md(Ci): defined methods TC: Total number of classes At first sight, we might be tempted to think that inheritance should be used extensively. However, the composition of several inheritance relations builds a directed acyclic graph (inheritance hierarchy tree), whose depth and width make understandability and testability fade away quickly [1,2,3,4]. Attribute Inheritance Factor (AIF)AIF can be calculated by using the following mathematical formula:  Where, Ah(Ci) = hidden attributes in class Ci Ad(Ci) = Av(Ci) + Ah(Ci): attributes defined in Ci Av(Ci): visible attributes in class Ci TC: Total number of classes Coupling Factor (COF)It measures the coupling between classes. COF can be calculated by using the following mathematical formula:  Where, is_client(Cc,Cs) =| 1 if (Cc⇒Cs)^(Cc≠Cs) , 0 otherwise TC: It denotes the total number of classes. The client-supplier relation, represented by Cc ⇒ Cs, means that Cc (client class) contains at least one noninheritance reference to a feature (method or attribute) of class Cs (supplier class). The COF numerator represents the actual number of coupling not imputable to inheritance 2, 3, 4, and 6. It is desirable that classes communicate with as few other classes as possible, and that they exchange as little information as possible. Coupling relations increase complexity, reduce encapsulation and potential reuse, and limit understandability and maintainability. Also, coupling in software systems has a strong negative impact on software quality, and therefore should be kept to the minimum during the design phase. However, for a given application, classes must cooperate to deliver some kind of functionality. Therefore, COF is expected to be lower bounded 2, 3, and 4. Polymorphism Factor (POF)Polymorphism means having the ability to take several forms. In OO systems, polymorphism allows the implementation of a given operation to be dependent on the object that "contains" the operation 2, 3, 4, and 6.  Where, Mo(Ci): overriding Methods in class Ci Mn(Ci): new Methods in class Ci DC(Ci): number of Descendants of Class Ci (derived classes) TC: Total number of Classes The POF numerator represents the actual number of possible different polymorphic situations. A given message sent to class Ci can be bound, statistically or dynamically, to a named method implementation which may have as many shapes as the number of times this same method is overridden (in Ci descendants) 2, 3, 4. Polymorphism arises from inheritance. Binding (usually at run time) a common message call to one of several classes (in the same hierarchy) is supposed to reduce complexity and to allow refinement of the class hierarchy without side effects. On the other hand, to debug such a hierarchy, by tracing the control flow, this same polymorphism would make the job harder. Therefore, polymorphism ought to be bounded within a certain range 2, 3, 4. Evaluation of MOOD FactorsThe grade awarded to an object-oriented program depends on the following table that is based on experiments.
The final grade is computed by using the following steps: Step 1: For all the indicators do the following: IF the indicator value is found within the specified range, THEN GRADE = 100% ELSE IF the indicator value is located in the tolerance range, THEN 60%≤GRADE by using interpolation. ELSE, the indicator outside the tolerance range, then GRADE<60% by using interpolation formula and the system should trigger the programmer's attention to a problem. 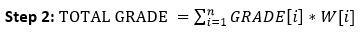 Where, GRADE [i]: the grade for the indicators i. W[i]: weight value assigned to the indicator to reflect its importance. n: It is the number of factors, n=6.  Where, FINAL GRADE: It represents the final grade of the evacuated object-oriented program [0:100]. TW: It represents the total weight that can be computed by using the following formula:  Where, n: the total number of indicators, n=6. W(Fi): the weight for indicator i. The grade of each indicator ranges from 0% to 100%. Each indicator is assigned a weight to reflect its importance. The classification of the six indicators is shown in the following table. This table is produced from reported study 2, 3, 4, 5, and 6.
Let's consider the following design patterns and evaluate their grade using MOOD factors.  Let's evaluate the grade for the above design pattern.
Base on the above evaluation, we have recommended the following:
We observe that each MOOD factor is associated with basic structural mechanisms of the object-oriented model. It is the mechanism that enables some recommendations for designers. The interval of each MOOD factor has been altered that is based on experimental results, to be fit in the evaluation of Java Programs. The weight factor reflects the importance of each characteristic. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Related Posts
Untouchable Number in Java
In this section, we will learn what is an untouchable number and also create Java programs to check if the given number is an untouchable number or not. The untouchable number program is frequently asked in Java coding interviews and academics. Untouchable Number A number N is called...
3 min read
Can Abstract Classes Have Static Methods in Java
? Java classes that cannot be instantiated but can offer a set of methods and attributes for their concrete subclasses to implement are known as abstract classes. Abstract classes are frequently utilized to build a group of similar classes that share some behaviors but differ in other...
4 min read
Java Program To Print Even Length Words in a String
Given a string str, write a Java program to print all words with even length in the given string. Example 1: Input: t= She sells seashells by the seashore Output: By Seashore Example 2: Input: t= To be or not to be, that is the question Output: To be or to that is question Approach: Using split() method The split() method is a...
2 min read
Object Life Cycle in Java
Based on the idea of object-oriented programming, or OOP, Java is a flexible and popular programming language. Everything in Java is an object, and objects go through many stages in their lifetime. In order to ensure proper resource management and program functioning, Java developers need to...
4 min read
DecimalFormat getPositivePrefix() method in Java
The Java DecimalFormat class's getPositivePrefix() method is used to retrieve this DecimalFormat instance's positive prefix value. Syntax: public String getPositivePrefix() Parameters: No parameter is accepted by this method. Return Value: The positive prefix value of this DecimalFormat object is returned by this method. Example 1: The formatting options for numeric numbers...
2 min read
Java Code for DES
Our dependency on the internet is increasing day by day and we share lots of personal information with others. Since our data or personal information is not secure. For this reason, the security of the data become essential for us. We need to keep data confidential,...
6 min read
Identical Linked List in Java
Identical linked lists are two linked lists with the same data in the same order. To determine if two linked lists are similar in Java, we compare corresponding nodes iteratively or recursively. It involves checking both the data and structure until all nodes match or a...
8 min read
Chained Exceptions in Java
In Java, a chained exception is a technique that enables programmers to associate one Exception with another. By providing additional information about a specific exception, debugging can be made easier. A chained exception is created by wrapping an existing exception in a new exception, which becomes...
6 min read
Java Cron Expression
The technology is constantly changing day by day. Sometimes, we are required to execute a job periodically on the server. Running the job on the server manually is a difficult task so, it cannot be done multiple times by the user or administrator. In order to...
8 min read
Why String is Immutable or Final in Java
? In object-oriented programming, the immutable string or objects that cannot be modified once it is created. But we can only change the reference to the object. We restrict to change the object itself. The String is immutable in Java because of the security, synchronization and concurrency,...
4 min read
Subscribe to Tpoint Tech
We request you to subscribe our newsletter for upcoming updates.

We provides tutorials and interview questions of all technology like java tutorial, android, java frameworks
Contact info
G-13, 2nd Floor, Sec-3, Noida, UP, 201301, India

