DevOpsDays InSpec Workshop
- 1. Building Security Into Your Workflow with InSpec Mandi Walls | [email protected]
- 2. HI! • Mandi Walls • Technical Community Manager for Chef, EMEA • [email protected] • @lnxchk • https://inspec.io • https://dev-sec.io/
- 3. EVERY business is a software business We’re going to be a software company with airplanes. – CIO, Alaska Airlines
- 4. What We Have Here Is A Communications Problem
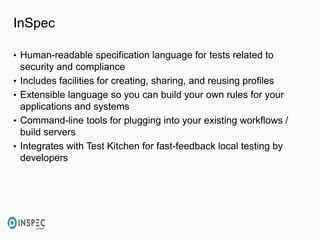
- 7. InSpec • Human-readable specification language for tests related to security and compliance • Includes facilities for creating, sharing, and reusing profiles • Extensible language so you can build your own rules for your applications and systems • Command-line tools for plugging into your existing workflows / build servers • Integrates with Test Kitchen for fast-feedback local testing by developers
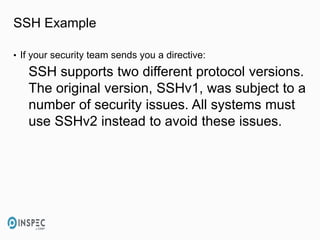
- 8. SSH Example • If your security team sends you a directive: SSH supports two different protocol versions. The original version, SSHv1, was subject to a number of security issues. All systems must use SSHv2 instead to avoid these issues.
- 9. How Do You Go About Fixing It? • Identify the file and file location to check your systems • Create a file with a new setting • Push out changes • What’s the plan for the currently used images? Rebuild? Remediate at instantiation? • Did you test it?
- 10. Lifecycle • When you get a mandate from security, how often is it checked? • Single big scan, report mailed out with a “due date”? • Yearly or twice-yearly massive scans with remediation projects?
- 11. Using InSpec User: chef Pass: dodams2018
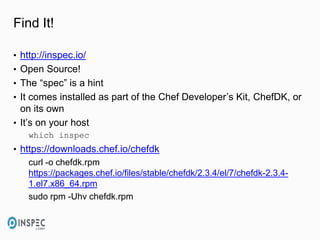
- 12. Find It! • http://inspec.io/ • Open Source! • The “spec” is a hint • It comes installed as part of the Chef Developer’s Kit, ChefDK, or on its own • It’s on your host which inspec • https://downloads.chef.io/chefdk curl -o chefdk.rpm https://packages.chef.io/files/stable/chefdk/2.3.4/el/7/chefdk-2.3.4- 1.el7.x86_64.rpm sudo rpm -Uhv chefdk.rpm
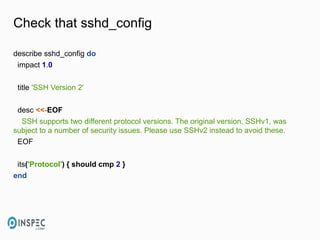
- 13. Check that sshd_config describe sshd_config do impact 1.0 title 'SSH Version 2' desc <<-EOF SSH supports two different protocol versions. The original version, SSHv1, was subject to a number of security issues. Please use SSHv2 instead to avoid these. EOF its('Protocol') { should cmp 2 } end
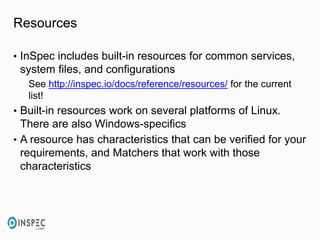
- 14. Resources • InSpec includes built-in resources for common services, system files, and configurations See http://inspec.io/docs/reference/resources/ for the current list! • Built-in resources work on several platforms of Linux. There are also Windows-specifics • A resource has characteristics that can be verified for your requirements, and Matchers that work with those characteristics
- 15. • Resources take the “grep for x” out of the testing phase • Parsers included in the InSpec software do the work for you • It’s built off the premises of rSpec, and meant to be human readable
- 16. its.... should... • it { should exist } • it { should be_installed } • it { should be_enabled } • its('max_log_file') { should cmp 6 } • its('exit_status') { should eq 0 } • its('gid') { should eq 0 }
- 17. Run It • InSpec is command line Installs on your workstation as a ruby gem or as part of the ChefDK • Can be run locally, test the machine it is executing on • Or remotely InSpec will log into the target and run the tests for you • Also a REPL https://www.inspec.io/docs/reference/shell/
- 18. Create a Basic Test – test.rb • Let’s write a basic test to make sure /tmp is a directory • It also should be owned by root • And its mode should be 01777 – open to all (plus sticky bit!) • Let’s check out the docs for the “file” resource for InSpec
- 19. File Resources in InSpec • https://www.inspec.io/docs/reference/resources/file/ • We want: Directory Owner Mode describe file(‘path’) do it { should MATCHER ‘value’ } end
- 20. test.rb describe file("/tmp") do it { should exist } its('type') { should cmp 'directory' } its('owner') { should eq 'root' } its('mode') { should cmp '01777' } end
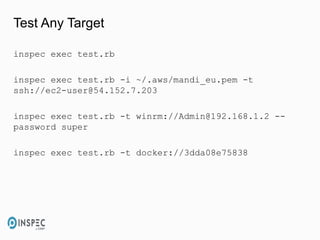
- 21. Test Any Target inspec exec test.rb inspec exec test.rb -i ~/.aws/mandi_eu.pem -t ssh://[email protected] inspec exec test.rb -t winrm://[email protected] -- password super inspec exec test.rb -t docker://3dda08e75838
- 22. Execute InSpec [chef@ip-172-31-38-151 ~]$ inspec exec ./test.rb Profile: tests from ./test.rb Version: (not specified) Target: local:// File /tmp ✔ should exist ✔ should be directory ✔ should be owned by "root" ✔ mode should cmp == "01777" Test Summary: 4 successful, 0 failures, 0 skipped
- 23. Failures • InSpec runs with failed tests return a non-zero return code Profile Summary: 0 successful, 1 failures, 0 skipped [chef@ip-172-31-29-25 ~]$ echo $? 1 [chef@ip-172-31-29-25 ~]$ • Passing tests have 0 return code Profile Summary: 1 successful, 0 failures, 0 skipped [chef@ip-172-31-29-25 ~]$ echo $? 0 [chef@ip-172-31-29-25 ~]$
- 24. Profiles • InSpec profiles allow you to package and share sets of InSpec tests for your organization or for a specific application set • Each profile can have multiple test files included • The test files generally test for one required outcome, but can look at different objects to meet requirements • Flexible! Create your own profiles for specific software you use
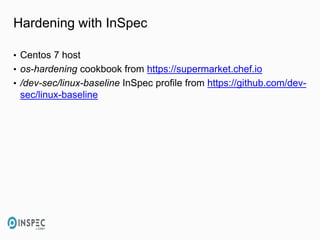
- 25. Hardening with InSpec • Centos 7 host • os-hardening cookbook from https://supermarket.chef.io • /dev-sec/linux-baseline InSpec profile from https://github.com/dev- sec/linux-baseline
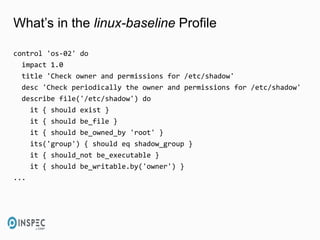
- 26. What’s in the linux-baseline Profile control 'os-02' do impact 1.0 title 'Check owner and permissions for /etc/shadow' desc 'Check periodically the owner and permissions for /etc/shadow' describe file('/etc/shadow') do it { should exist } it { should be_file } it { should be_owned_by 'root' } its('group') { should eq shadow_group } it { should_not be_executable } it { should be_writable.by('owner') } ...
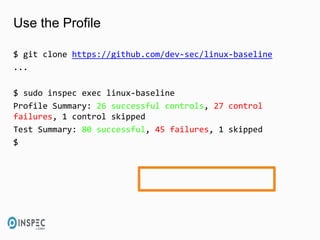
- 27. Use the Profile $ git clone https://github.com/dev-sec/linux-baseline ... $ sudo inspec exec linux-baseline Profile Summary: 26 successful controls, 27 control failures, 1 control skipped Test Summary: 80 successful, 45 failures, 1 skipped $
- 28. What’s in the os-hardening Cookbook
- 29. Use Chef to Repair the Findings $ chef generate cookbook harden (ignore git's complaints, it's ok)
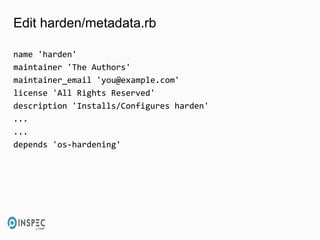
- 30. Edit harden/metadata.rb name 'harden' maintainer 'The Authors' maintainer_email '[email protected]' license 'All Rights Reserved' description 'Installs/Configures harden' ... ... depends 'os-hardening'
- 31. Create a Cookbooks Package $ cd harden $ berks install $ berks package $ cd .. $ tar –xzvf harden/cookbooks-VERSION.tar.gz
- 32. Run chef-client to remediate failed tests $ sudo chef-client -r "recipe[os-hardening]" --local-mode
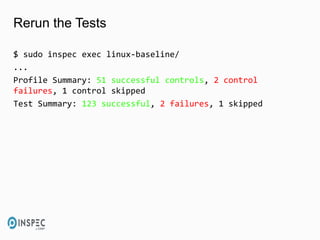
- 33. Rerun the Tests $ sudo inspec exec linux-baseline/ ... Profile Summary: 51 successful controls, 2 control failures, 1 control skipped Test Summary: 123 successful, 2 failures, 1 skipped
- 34. What’s Still Failing? • Find the controls that aren’t passing • Decide if you want to fix them or forget them • Let’s fix one and forget the others
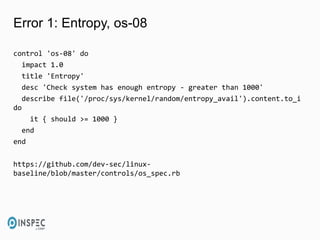
- 35. Error 1: Entropy, os-08 control 'os-08' do impact 1.0 title 'Entropy' desc 'Check system has enough entropy - greater than 1000' describe file('/proc/sys/kernel/random/entropy_avail').content.to_i do it { should >= 1000 } end end https://github.com/dev-sec/linux- baseline/blob/master/controls/os_spec.rb
- 36. Fix it with rngd $ vi harden/recipes/default.rb package 'rng-tools' service 'rngd' do action [:start, :enable] end Install the Package Turn on the Service
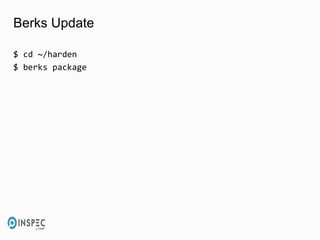
- 37. Berks Update $ cd ~/harden $ berks package
- 38. Install new cookbooks and run chef-client $ cd ~ $ tar –xzvf harden/cookbooks-NEWVERSION.tar.gz $ sudo chef-client –r “recipe[harden],recipe[os- hardening]” --local-mode … Recipe: harden::default * yum_package[rng-tools] action install - install version 0:5-13.el7.x86_64 of package rng-tools * service[rngd] action start - start service service[rngd] * service[rngd] action enable (up to date)
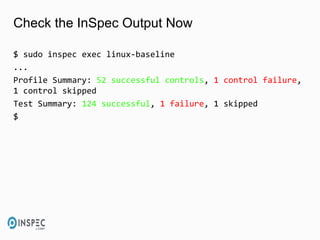
- 39. Check the InSpec Output Now $ sudo inspec exec linux-baseline ... Profile Summary: 52 successful controls, 1 control failure, 1 control skipped Test Summary: 124 successful, 1 failure, 1 skipped $
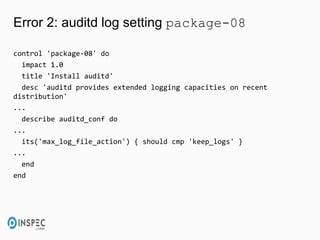
- 40. Error 2: auditd log setting package-08 control 'package-08' do impact 1.0 title 'Install auditd' desc 'auditd provides extended logging capacities on recent distribution' ... describe auditd_conf do ... its('max_log_file_action') { should cmp 'keep_logs' } ... end end
- 41. Maybe We're Ok with the Current Setting • Large InSpec profiles contain lots of rules • You may not want or need all of them for your infrastructure • You can pick and choose which ones you want using your profile • Let's ignore the auditd log file setting for now
- 42. Building New Profiles $ inspec init profile my_hardening Create new profile at /home/chef/my_hardening * Create file README.md * Create directory controls * Create file controls/example.rb * Create file inspec.yml * Create directory libraries $
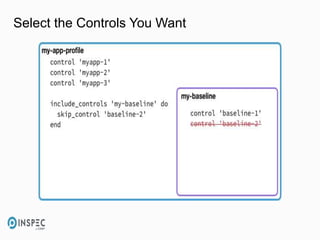
- 43. Select the Controls You Want
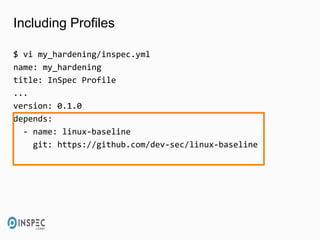
- 44. Including Profiles $ vi my_hardening/inspec.yml name: my_hardening title: InSpec Profile ... version: 0.1.0 depends: - name: linux-baseline git: https://github.com/dev-sec/linux-baseline
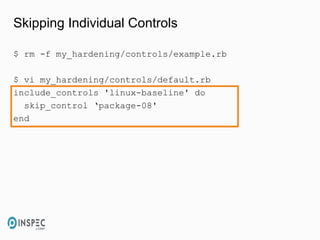
- 45. Skipping Individual Controls $ rm -f my_hardening/controls/example.rb $ vi my_hardening/controls/default.rb include_controls 'linux-baseline' do skip_control ‘package-08' end
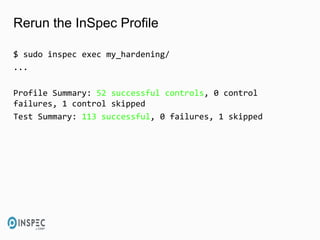
- 46. Rerun the InSpec Profile $ sudo inspec exec my_hardening/ ... Profile Summary: 52 successful controls, 0 control failures, 1 control skipped Test Summary: 113 successful, 0 failures, 1 skipped
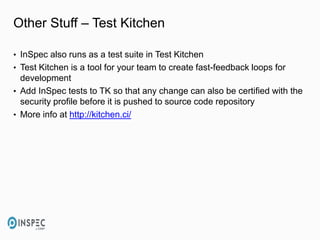
- 47. Other Stuff – Test Kitchen • InSpec also runs as a test suite in Test Kitchen • Test Kitchen is a tool for your team to create fast-feedback loops for development • Add InSpec tests to TK so that any change can also be certified with the security profile before it is pushed to source code repository • More info at http://kitchen.ci/
- 48. Resources • https://inspec.io • https://dev-sec.io • https://github.com/chef-training/workshops/ • http://www.anniehedgie.com/inspec-basics-1 • Windows and InSpec: http://datatomix.com/?p=236 • https://blog.chef.io/category/inspec/ • We're hiring! Work on InSpec in Belfast! https://chef.io/careers
Editor's Notes
- #5: Compliance requirements are often set out in flat documents. Sometimes PDFs, sometimes other formats, but they have a tendency to be a huge list of characteristics and checkboxes to be investigated and potentially remediated. Security tools may be somewhat more flexible, encoded into a set of shell scripts that check and verify the systems after they are built. But what if it was easy to build these checks into the workflow while the systems are being built and applications installed.
- #6: For the purposes of compliance, we actually wanted a common language, in code, that would allow all audiences – compliance, security, and devops – to collaborate on. And this code will then act on systems. This is whyInSpec was developed.
- #11: For bits like the ssh configuration that are considered more infrastructure than application, these practices are common, changes are periodically rolled into the source images for new hosts (or containers) and the old configurations are eventually purged from production. It’s a herd-immunity approach. But what happens if the thing to be tested is affected by a continuously developed application? Like run time configurations for java, or your databases. Can you count on every team to always know all of the requirements?
- #24: Plug InSpec into whatever command set you are already using
- #48: If there is time, run a short InSpec and Kitchen demo.









![Execute InSpec
[chef@ip-172-31-38-151 ~]$ inspec exec ./test.rb
Profile: tests from ./test.rb
Version: (not specified)
Target: local://
File /tmp
✔ should exist
✔ should be directory
✔ should be owned by "root"
✔ mode should cmp == "01777"
Test Summary: 4 successful, 0 failures, 0 skipped](https://image.slidesharecdn.com/walls-dodams2018-inspecworkshop-180627085554/85/DevOpsDays-InSpec-Workshop-22-320.jpg)
![Failures
• InSpec runs with failed tests return a non-zero return code
Profile Summary: 0 successful, 1 failures, 0 skipped
[chef@ip-172-31-29-25 ~]$ echo $?
1
[chef@ip-172-31-29-25 ~]$
• Passing tests have 0 return code
Profile Summary: 1 successful, 0 failures, 0 skipped
[chef@ip-172-31-29-25 ~]$ echo $?
0
[chef@ip-172-31-29-25 ~]$](https://image.slidesharecdn.com/walls-dodams2018-inspecworkshop-180627085554/85/DevOpsDays-InSpec-Workshop-23-320.jpg)



![Run chef-client to remediate failed tests
$ sudo chef-client -r "recipe[os-hardening]" --local-mode](https://image.slidesharecdn.com/walls-dodams2018-inspecworkshop-180627085554/85/DevOpsDays-InSpec-Workshop-32-320.jpg)

![Fix it with rngd
$ vi harden/recipes/default.rb
package 'rng-tools'
service 'rngd' do
action [:start, :enable]
end
Install the Package
Turn on the Service](https://image.slidesharecdn.com/walls-dodams2018-inspecworkshop-180627085554/85/DevOpsDays-InSpec-Workshop-36-320.jpg)
![Install new cookbooks and run chef-client
$ cd ~
$ tar –xzvf harden/cookbooks-NEWVERSION.tar.gz
$ sudo chef-client –r “recipe[harden],recipe[os-
hardening]” --local-mode
…
Recipe: harden::default
* yum_package[rng-tools] action install
- install version 0:5-13.el7.x86_64 of package
rng-tools
* service[rngd] action start
- start service service[rngd]
* service[rngd] action enable (up to date)](https://image.slidesharecdn.com/walls-dodams2018-inspecworkshop-180627085554/85/DevOpsDays-InSpec-Workshop-38-320.jpg)