I'm an absolute newbie when it comes to all this side of reverse engineering. Each time I try and understand it, I get lost almost immediately.
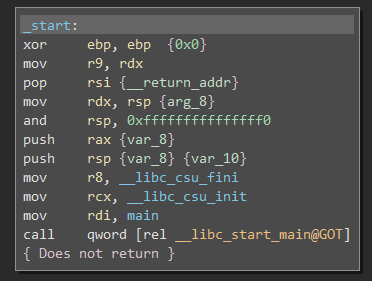
I am trying a lab. I open it up in Binary Ninja. I get the following
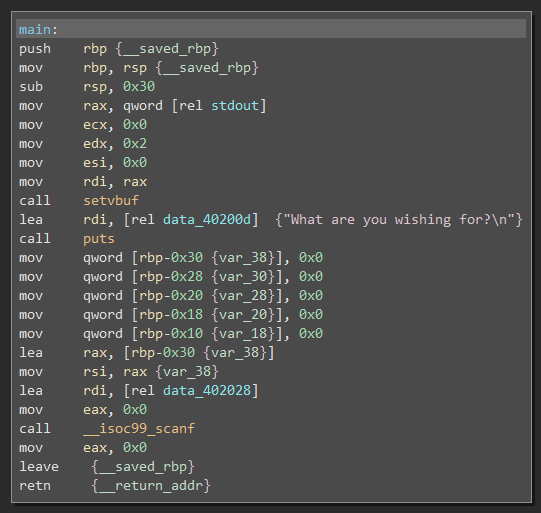
When I open main I get the following
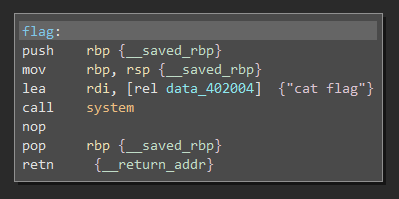
Nothing much seems to happen but there is a function(?) called flag that looks like what I need
When I copy the address, it comes out as:
0x401152
I'm trying to do stuff like this on the command line but getting nowhere fast
python3 -c "print (28 * 'A' + '\x52\x11\x40')" | ./santa;
I then try to iterate through and no luck although I do get a segmentation fault on the 53rd iteration
for i in {0..60}; do python3 -c "print ($i * 'A' + '\x52\x11\x40')" | ./santa; done
Any pointers? I'm absolutely lost