This Action will connect to a provided AZURE key vault as input and will loop through each secret key (server name). For each server, automatically generate a random unique password (default 24char), set that password against the VM and save the password value against the relevant secret key in the key vault. This will allow you to automate, maintain and manage all your server passwords from a centrally managed key vault in AZURE by only giving relevant access when required by anyone via key vault permissions.
- The Azure key vault must be pre-populated with
Secret Keys, where eachkeyrepresents a server name:
See this tutorial on setting up the Azure key vault and GitHub Secret Credential (if needed).
| Inputs | Required | Description | Default |
|---|---|---|---|
| key-vault-name | True | Name of the Azure key vault pre-populated with secret name keys representing server names hosted in Azure. | N/A |
| password-length | False | The amount of characters in the password. | 24 |
Copy and paste the following snippet into your .yml file.
- name: Rotate VMs administrator passwords
uses: Pwd9000-ML/[email protected]
with:
key-vault-name: ${{ env.KEY_VAULT_NAME }}
password-length: 24 ##Optional configurationHere is a link to an example workflow file using legacy authentication (Client and Secret).
name: Update Azure VM passwords
on:
workflow_dispatch:
schedule:
- cron: '0 9 * * 1' ##Runs at 9AM UTC every Monday##
jobs:
publish:
runs-on: windows-latest
env:
KEY_VAULT_NAME: 'your-key-vault-name'
steps:
- name: Check out repository
uses: actions/[email protected]
- name: Log into Azure using github secret AZURE_CREDENTIALS
uses: Azure/[email protected]
with:
creds: ${{ secrets.AZURE_CREDENTIALS }}
enable-AzPSSession: true
- name: Rotate VMs administrator passwords
uses: Pwd9000-ML/[email protected]
with:
key-vault-name: ${{ env.KEY_VAULT_NAME }}Here is a link to an example workflow file (OIDC) using Open ID Connect(OIDC).
name: Update Azure VM passwords
on:
workflow_dispatch:
schedule:
- cron: '0 9 * * 1' ##Runs at 9AM UTC every Monday##
permissions:
id-token: write
contents: read
jobs:
rotatePwd:
runs-on: windows-latest
env:
KEY_VAULT_NAME: 'your-key-vault-name'
steps:
- name: Check out repository
uses: actions/[email protected]
- name: 'Az CLI login using OIDC'
uses: azure/login@v1
with:
client-id: ${{ secrets.AZURE_CLIENT_ID }}
tenant-id: ${{ secrets.AZURE_TENANT_ID }}
subscription-id: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
enable-AzPSSession: true
- name: Rotate VMs administrator passwords
uses: Pwd9000-ML/[email protected]
with:
key-vault-name: ${{ env.KEY_VAULT_NAME }}-
You can use the AzurePreReqs.ps1 (legacy) script to create a key vault, generate a GitHub Secret to use as
AZURE_CREDENTIALSand sets relevant RBAC access on the key vault,Key Vault Officer, as well asVirtual Machine Contributorover virtual machines in the Azure subscription. -
You can use the AzurePreReqs-OIDC.ps1 (modern) script to create a key vault, generate a federated GitHub principal to authenticate (passwordless) to Azure using only the following GitHub secrets:
secrets.AZURE_CLIENT_ID,secrets.AZURE_TENANT_ID,secrets.AZURE_SUBSCRIPTION_ID. The script also sets relevant RBAC access on the key vault,Key Vault Officer, as well asVirtual Machine Contributorover virtual machines in the Azure subscription. -
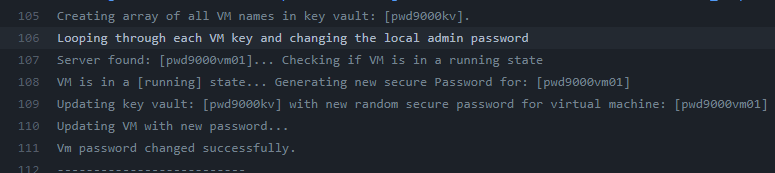
Passwords will only be rotated for
secrets/namesof servers populated in the key vault assecretkeys. Only virtual machines that are in arunningstate will have their passwords rotated:
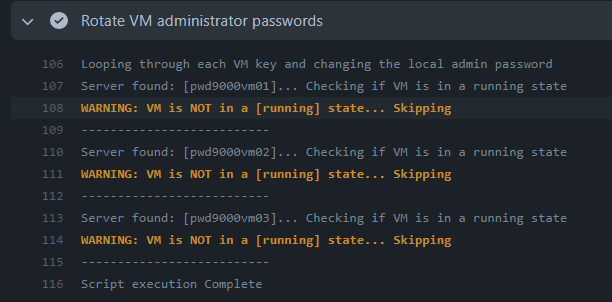
- Servers will be skipped if they are not running:
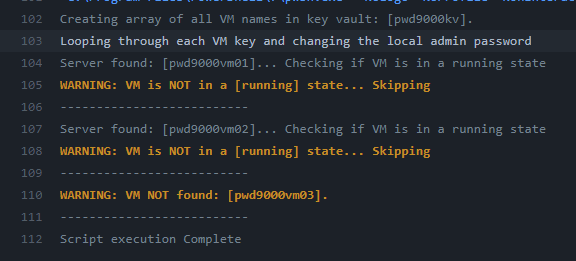
- If a server does not exist or the GitHub Secret
AZURE_CREDENTIALSdoes not have access over the Virtual Machine a warning is issued of 'VM NOT found':
- DO NOT populate the key vault with servers that act as Domain Controllers.
As of release v1.1.0; Support for linux and windows runner types now available.
| Environment | YAML Label |
|---|---|
| Windows Server 2022 | windows-2022 |
| Windows Server 2019 | windows-latest or windows-2019 |
| Windows Server 2016 (deprecated ) | windows-2016 |
| Ubuntu 20.04 | ubuntu-latest or ubuntu-20.04 |
| Ubuntu 18.04 | ubuntu-18.04 |
The associated scripts and documentation in this project are released under the MIT License.