Additional Contributor: Claire Fulk
Secure Access served as the primary method of securing DNS-layer traffic for the GovWare 2025 Security Operations Centre (SOC). Two virtual appliances were configured on the UCS M8 in the ‘SOC in a Box’ for outbound requests to flow through, which provided more detailed traffic information like the initiator IP address, destination domain, content category and disposition to the SOC team while resolving DNS traffic. Two appliances were deployed to ensure redundancy during the conference, and logs were forwarded to Cisco XDR and Splunk for network-wide correlation.
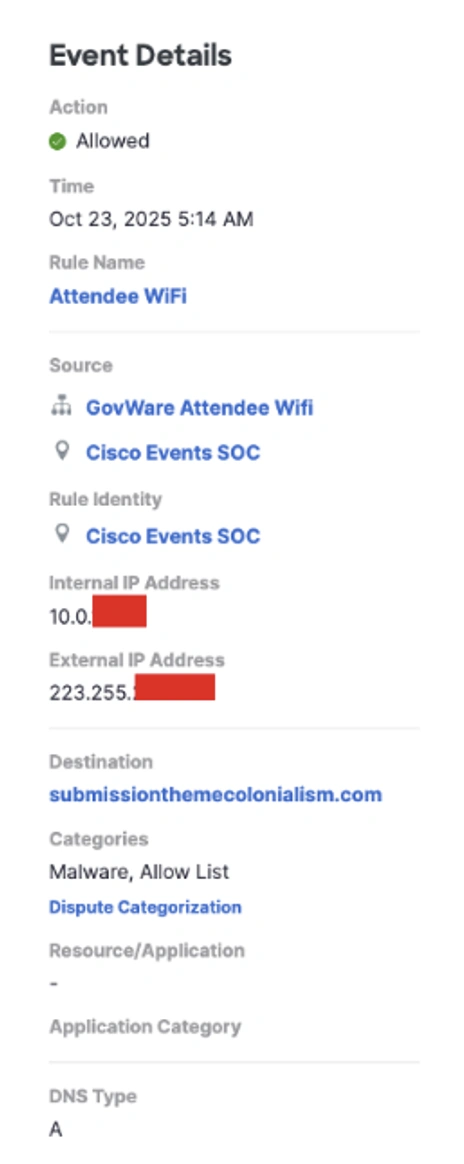
Secure Access immediately provided valuable insight on day one with the detection of our first phishing attack. On 21 October, 6:15 UTC, Secure Access flagged a DNS request to a site categorized as malware despite the seemingly innocent URL.
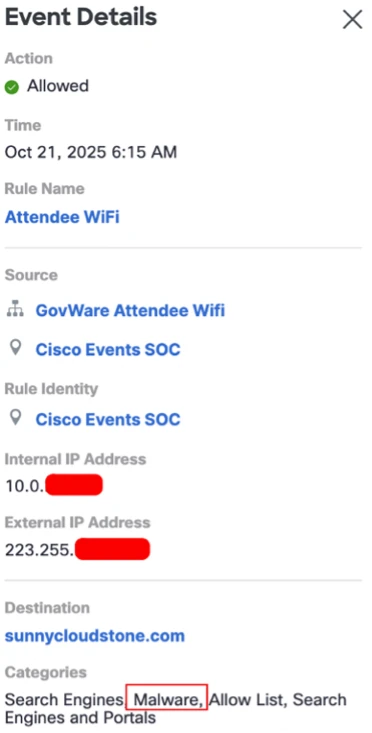
After further inspection, this aligned with a known phishing campaign which uses a random three-word domain pattern and associated with the same domain server.
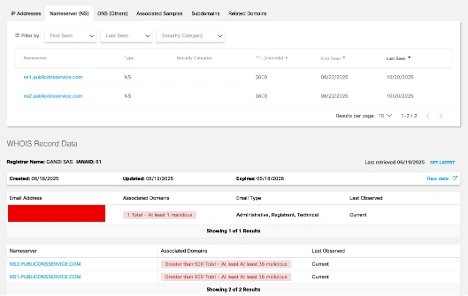
Upon validating the destination’s nefarious purpose, swift action was taken in Secure Access, and traffic was blocked from making a connection. This was my first experience as a SOC analyst, and I was empowered by the integrated security technology and managers to take the blocking action myself.
After blocking the first malicious domain, Cisco XDR flagged an associated domain was being reached out to by the same endpoint. It was observed that during this phishing attempt, the compromised endpoint would attempt to connect to multiple destinations, to try to get past security controls. The destination caught by Cisco XDR was considered a newly seen domain and not yet flagged as malicious, but after further investigation, it was confirmed to be part of the attack.
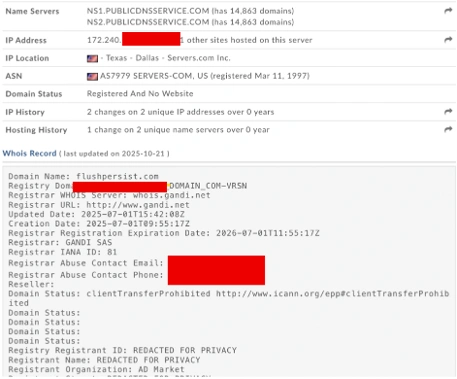
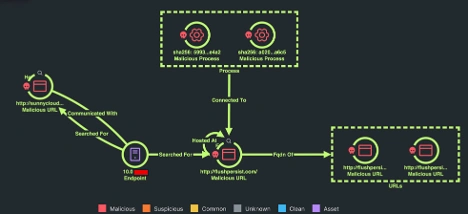
All associated destinations were then blocked on Secure Access to prevent any connections, and an incident report was submitted to the GovWare team.
Later in the conference, a similar event occurred following the same formula. Secure Access flagged the first destination as malware, and the team validated the site as malicious.
At the same time, a sudden influx of requests to sites categorized as Newly Seen Domains came flooding in.
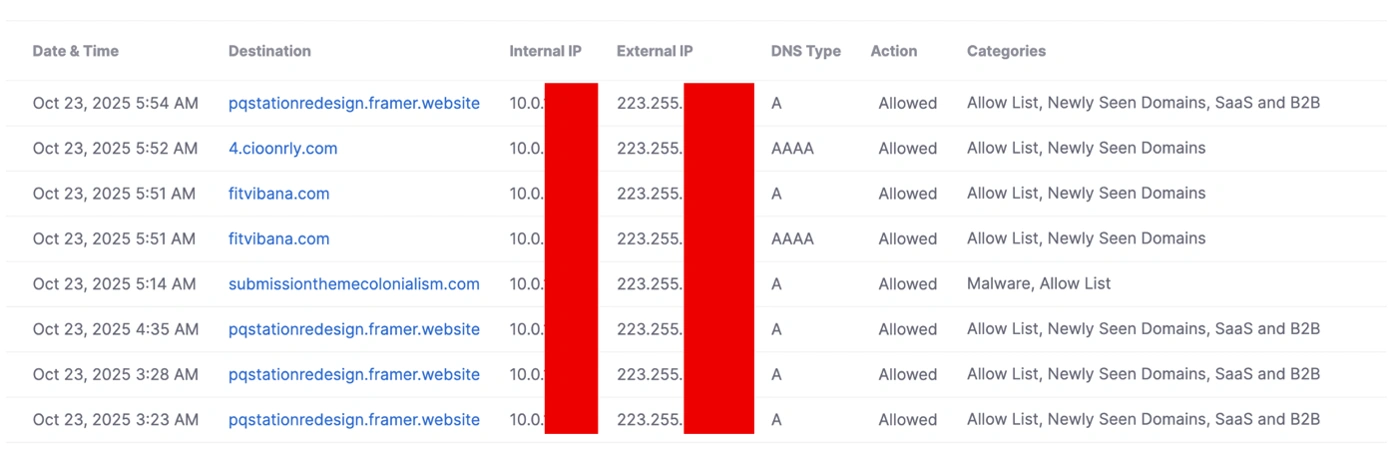
Our SOC incident response team confirmed that the newly seen domains were associated with the attack, and one would load malicious java script (.js). Upon this discovery, traffic pointing to these destinations were blocked and a report submitted to GovWare. This proved that the attack has evolved from reaching out to one type of destination to reaching out to multiple domains in succession.
As a whole, the traffic at GovWare 2025 was business-as-usual, but it only takes one successful incident to take out an entire enterprise.
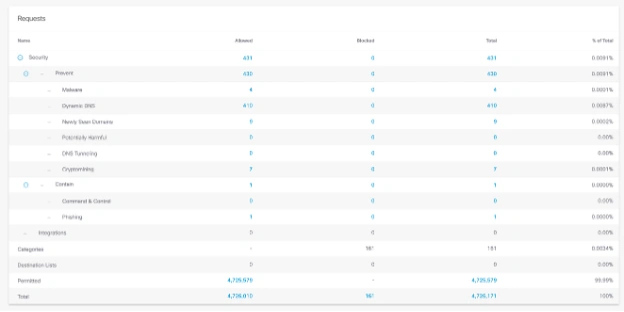
An unexpected observation during the security conference was the spike in Adult and Pornographic content attendees were trying to access during the lunch period. The team was given approval to block both content categories on the GovWare2025 Wi-Fi connection.
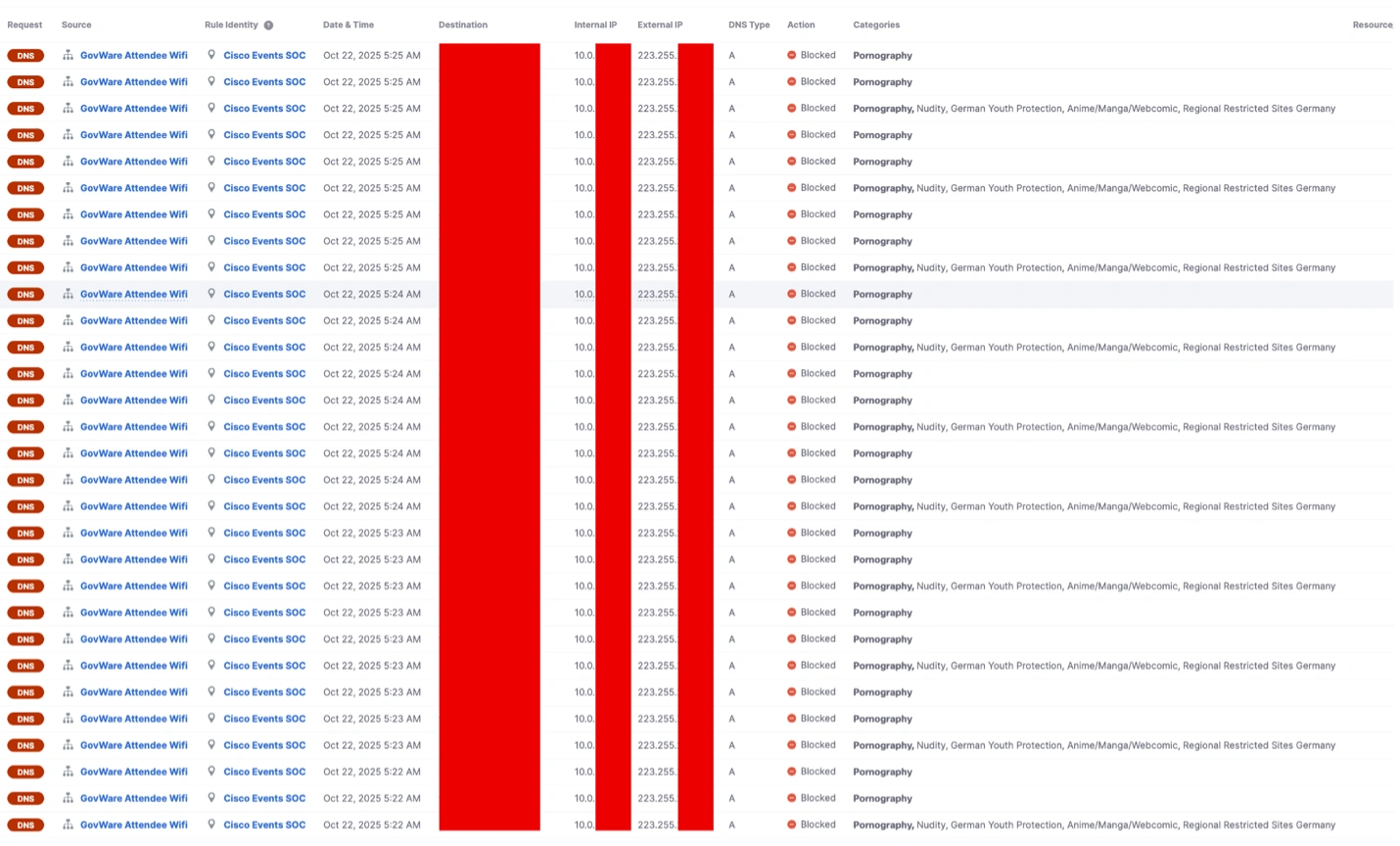
While this may not immediately jump out as a security threat, it does show that even the most security-minded individuals attending a conference dedicated to keeping this industry safe are still human. And the biggest risk to a network are the humans on it. Social engineering preys on the humanity of a network and recognizes that even those educated in safe internet practices can be influenced to click on a link if it specifically appeals to something that interests them. The initial site itself may not be harmful, but many of these sites are known to contain pop-up ads containing malware, and if a user is utilizing a secured network to access these resources, they have just become the vulnerability they dedicate their career to preventing.
Check out the other blogs by my colleagues in the GovWare SOC.
About GovWare
GovWare Conference and Exhibition is the region’s premier cyber information and connectivity platform, offering multi-channel touchpoints to drive community intel sharing, training, and strategic collaborations.
A trusted nexus for over three decades, GovWare unites policymakers, tech innovators, and end-users across Asia and beyond, driving pertinent dialogues on the latest trends and critical information flow. It empowers growth and innovation through collective insights and partnerships.
Its success lies in the trust and support from the cybersecurity and broader cyber community that it has had the privilege to serve over the years, as well as organisational partners who share the same values and mission to enrich the cyber ecosystem.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media






CONNECT WITH US