Disclaimer: The views expressed in this post are my own and do not reflect those of Okta or its affiliates.
This write-up walks through how to set up Auth0 as a SAML Identity Provider (IdP) with Microsoft Entra ID, specifically to support external user login to SharePoint Online without needing to pre-create their accounts in Azure AD.
It’s especially useful if you already manage your external customers or partners in Auth0 and want Microsoft Entra to take care of Just-in-Time (JIT) provisioning the first time a user logs in.
While Okta Workforce Identity is a more complete solution for this scenario, the same can be achieved using Auth0 — especially if you're already using Auth0 to manage authentication for other apps.
Let's assume that users do not yet exist in Auth0. They will be created at the time of login via an invite flow built through sharepoint site, your app or signup portal.
Flow
- Let external users authenticate through Auth0
- Redirect login requests from Microsoft Entra to Auth0
- Automatically create the user in Microsoft Entra ID (JIT) when they log in for the first time
- Grant access to SharePoint Online
Set Up a SAML Connection in Auth0
- Go to Auth0 Dashboard → Applications → Applications → + Create Application
- Name it something like
SAML for Entra - Choose Regular Web Application
- Name it something like
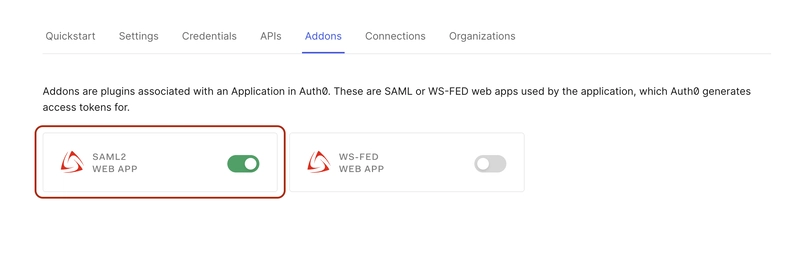
- In the newly created application, go to Addons → Enable SAML2 Web App
Once enabled, it pops up a few configurations, simply click on download
- From the
usagetab, switch over to thesettingstab and don't forget to paste this -https://login.microsoftonline.com/login.srfin the Application Callback URL. The SAML token will be posted in this URL when the user tries to sign in.
- Close the SAML add on pop up and navigate to the
settingstab of your Regular Web App, scroll down to the section that says -Application URIsand make sure that you place the same URL on these 3 input fields -Allowed Callback URLs,Allowed Logout URLs,Allowed Web Origins
Configure Microsoft Entra to Trust Auth0
- Go to Microsoft Entra Admin Center
- Navigate to: Entra ID → External Identities → All Identity Providers → Custom
- Click Add new > SAML/WS-Fed
- Fill in the following:
- Display name: Auth0 Federation
- Protocol: SAML
-
Domain name of federating IdP: You can put down the domain name from your Auth0 Regular Web App. To fetch that, go to your Auth0 Tenant > Applications > Saml for Entra > Settings > Domain or if you'd like to use your own domain e.g.,
customers.example.com, you'd need to look at the next step on how to add DNS TXT Record for Federation Validation (the domain of the users you'll authenticate)
💡 In Auth0, domain names of apps are defined by the tenant name. However, if you'd want to learn more about custom domains, this is a good documentation to go over that - Custom Domains
After you've put in the domain in your Entra ID Tenant (Refer to the first image above), navigate to the dropdown field that says - Select a method for populating metadata
and choose - Parse metadata file, and upload the metadata XML downloaded from Auth0
Add DNS TXT Record for Federation Validation
If your Auth0 domain (e.g., your-tenant.auth0.com) does not match the email domain of your users (e.g., @customers.example.com), you'll need to prove domain ownership by adding a DNS TXT record.
In the DNS settings for customers.example.com, add:
@ IN TXT DirectFedAuthUrl=https://your-tenant.auth0.com/samlp/<client_id>
- Replace
<client_id>with the client ID of your Auth0 SAML app - Wait 10–30 minutes for the DNS to propagate
- Use tools like
nslookupor Google’s DIG to verify
Enable User Sign-ins using Auth0
Ensure that:
- The application has that database connection enabled under Connections → Database
- Optional: Customize the signin page using Auth0's Universal Login
For this demo - the name of my organization is Echoes Enterprise, and so I have kept the branding that way. You'll also see my sharepoint site url to be the same.
Invite the User in SharePoint
- To invite a user, navigate to the Sharepoint Site, and click on
Site Access.
- Enter the user's email (e.g.,
[email protected]) - Click Invite
- Go to your Auth0 Tenant and now
create the same user
The user will receive a link to access the resource. When they click it:
- Microsoft Entra detects the federated domain
- Redirects to Auth0
- Auth0 authenticates the user
- Microsoft Entra JIT-provisions the user
- The user is granted access (e.g., SharePoint Online)
Success Criteria (What Happens Behind the Scenes) - Important for your understanding!
When the user clicks the invite link or tries to access SharePoint:
- Microsoft Entra detects the user’s email domain and recognizes it as federated.
- Entra redirects the login request to Auth0’s SAML endpoint.
- The user lands on Auth0’s Universal Login Page and enters their credentials.
- Auth0 authenticates the user, then issues a SAML Response back to Entra with claims like:
NameID(persistent format),emailaddress(optional), upn, name, etc. - Microsoft Entra validates the SAML assertion, and if successful:
- Creates a guest user (JIT)
- Grants access to the SharePoint resource
- At no point is the user created ahead of time in Entra — they are auto-provisioned upon first successful login.
To watch the end user flow for Alice, watch this video
🛠 Common Pitfalls
| Issue | Fix |
|---|---|
AADSTS50020 (user not found) |
Make sure the user was invited in Entra |
| Federation domain rejected | Add the required TXT record in DNS |
| Auth0 doesn't send correct claims | Check mappings and SAML Action overrides |
| JIT fails despite invite | Ensure SAML assertion contains NameID and emailaddress claims |
Final Thoughts
This integration allows you to decouple external user authentication from Azure AD, while still keeping governance within Microsoft Entra. It's ideal if you're managing users in Auth0 and want a seamless way to provide access to Microsoft resources — like SharePoint — without duplicating identities across systems.
















Top comments (0)