Hi there! I'm Maneshwar. Right now, I’m building LiveAPI, a first of its kind tool for helping you automatically index API endpoints across all your repositories. LiveAPI helps you discover, understand, and use APIs in large tech infrastructures with ease.
If you’ve ever duct-taped Keycloak, Okta, or Ping together just to manage authentication and identity for your apps, meet your new favorite tool: authentik — the authentication glue your infra stack deserves.
Self-hosted, open source, flexible as hell — authentik isn’t just another identity provider. It’s your one-stop solution to build robust auth flows that you own, you control, and you can scale, without handing your users’ data over to a SaaS black box.
Why Developers Love authentik
- Self-host anywhere: Docker, Kubernetes, Terraform — take your pick.
- Full-stack support: OIDC, SAML, SCIM, LDAP, RADIUS — yep, all the buzzwords.
- Customizable policies: Write reusable policies in Python for conditional access, MFA, app rules, etc.
- Extensible API: Automate workflows, user onboarding, group assignments, and more.
- Security-first: Transparent codebase, open reviews, and designed with Zero Trust in mind.
- It just works: From WebAuthn to passkeys, remote desktop access to legacy app integration.
Common Use Cases
- 🔐 Single Sign-On (SSO) for internal tools or customer-facing apps
- 🛡️ Zero Trust implementation without vendor lock-in
- 📦 Legacy Application Integration (think RDP, VNC, SSH)
- 🔄 Customer Identity Management with self-service and MFA
- 📡 API Gateway Authentication with conditional policies
A Quick Look at How It Works
Authentik wraps around your apps and services using a proxy model or identity protocol integration (OIDC/SAML). Here's a basic flow:
- App triggers login
- authentik intercepts and enforces policy (MFA? GeoIP? Time-based? Your call.)
- User authenticates via configured providers (LDAP, OAuth, SAML, social login, etc.)
- authentik issues token / assertion
- User gets in — if they meet your conditions
All configurable via UI or YAML-based IaC.
Dev Workflow Example
- Run Authentik, PostgreSQL, and Redis locally using Docker.
- Complete the initial setup with admin email and password.
- Create a new application in GitLab and obtain the client ID and secret.
- In the Authentik admin interface, set up a social login and federation for LiveAPI.
- Perform a basic test to verify login flow.
- Create an application for redirection and note the client ID and secret.
- Update the branding settings as needed.
1. Run Authentik, PostgreSQL, and Redis Locally
Generate .env secrets
echo "PG_PASS=$(openssl rand -base64 36 | tr -d '\n')" >> .env
echo "AUTHENTIK_SECRET_KEY=$(openssl rand -base64 60 | tr -d '\n')" >> .env
Start services
docker-compose up
2. Complete the initial setup with admin email and password.
Go to:
http://localhost:9000/if/flow/initial-setup/
Set your admin email and password. After setup, you should see:
3. Create a new application in GitLab and obtain the client ID and secret.
Go to:
https://gitlab.selfhosted.com/admin/applications
New application config
Use the following Redirect URIs:
http://localhost:9000/source/oauth/callback/liveapi/
Slug: Slug should be liveapi.
In the image ignore the second callback URL.

Checkbox:
- Trusted
- Confidential
- api
- read_user
- openid
- profile
✅ Check all 7 boxes (scope permissions)
Copy the client credentials:
-
Client ID:
e79ce2f11f1242cd35ee58eb6e306336b748d912614800bd03dc85741e14704e -
Client Secret:
gloas-8764d66a08c0eb96437946ff57ac44d8e1de663b228657d9d8dc91c35db253ff
4. In the Authentik admin interface, set up a social login and federation for LiveAPI.
Go to:
http://localhost:9000/if/admin/#/core/sources
→ Directory → Federation & Social Login → Create
Basic settings:
- Name:
liveapi - Slug:
liveapi - Enabled: ✅
Dropdowns:
-
User Matching Mode:
Use the user's email address, but deny enrolment when email already exists -
Group Matching Mode:
Use the group's name, but deny enrollment when the name alreday exits
Protocol Settings:
Scroll down to Protocal Settiings in same form
- Consumer Key: GitLab Client ID
- Consumer Secret: GitLab Client Secret
- Scopes:
api read_user openid profile email
OIDC Discovery URL:
https://gitlab.selfhosted.com/.well-known/openid-configurationAuth Method: Second radio button. Include Client ID + Secret as request params

Update identification stage
Go to:
http://localhost:9000/if/admin/#/flow/stages
→ Flows & Stages → Edit first form
- Select Available Sources (liveapi)
- Click the right arrow button
- Enable: Show Sources labels checkbox
5. Perform a basic test to verify login flow.
Go to:
http://localhost:9000/if/admin/#/flow/flows
→ Flows & Stages → default-authentication-flow → ▶ Play
It opens a form.
Copy the URL from the browser and open it in Incognito.
Click the LiveAPI login button → GitLab login should appear.
Example Auth URL:
http://localhost:9000/application/o/authorize/?client_id=DrH7UiiQdgTNy1WNvb68TP4iAahsprkW7WINZeOe&redirect_uri=http://localhost:3000&response_type=code&scope=openid
6. Create an application for redirection and note the client ID and secret.
Go to:
http://localhost:9000/if/admin/#/core/applications
→ Applications → Create with Provider
Follow the form steps and save.
Launch URL: http://localhost:3000

Scroll down, copy:
-
Authentik Client ID:
ftQ15cphF8DJ73cFMwQFFUcIfC6mH7tbtI0wcDvm -
Authentik Client Secret:
AZgdvsMdLmwqXzu3Rvk37JFBQhowThrwTDzvMPPCk0ZjZfVFIcFAmq09bNvQURaPbPS9KbAhBwaUNdjSj7oHX9zuZqZTUafM4lMltPOwFF6nhPix4g0DUkuCWIvQfhEx
Update the "User Write" Stage
Go to: http://localhost:9000/if/admin/#/flow/stages;%7B%22search%22%3A%22default-source-enrollment-write%22%7D


Test Final Redirect Flow
Try this URL (replace with your Authentik Client ID):
http://localhost:9000/application/o/authorize/?client_id=YOUR_CLIENT_ID&redirect_uri=http://localhost:3000&response_type=code&scope=openid
After logging in via GitLab, you'll be redirected to:
http://localhost:3000/?code=595daab4f51e45c8ab89cc9ea6c2f9bf&state=
You can now use the code to call Authentik’s token endpoint and fetch user info.
7. Update the branding settings as needed.
Set up your branding assets:
/static/dist/assets/icons/LogoPlusText.png
/static/dist/assets/icons/LALogo.png
/static/dist/assets/icons/LABg.png
Go to:
Sidebar → Brands
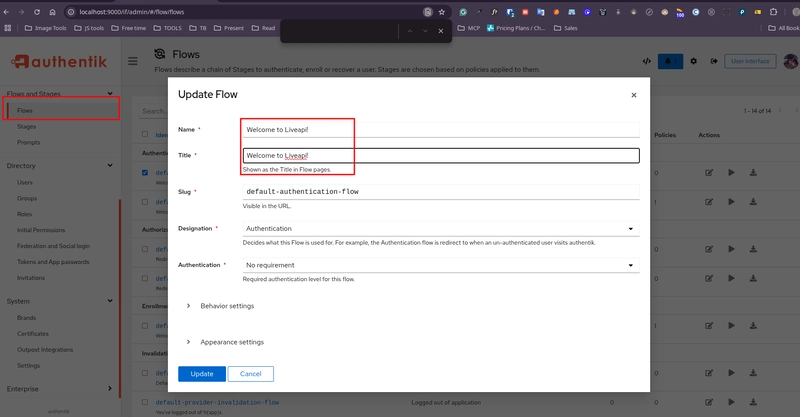
Change Welcome Text
Go to:
http://localhost:9000/if/admin/#/flow/flows
→ Edit the first flow
Enterprise Features, Without the Enterprise Tax
authentik punches way above its weight:
- WebAuthn (passkeys)
- GeoIP / Impossible Travel detection
- SCIM & LDAP provisioning
- Remote Access Gateway (RDP, SSH, VNC)
- App Proxy with full audit logging
- FIPS support for compliance-driven orgs
Real World Proof: CoreWeave
“With help from the Authentik Security team, CoreWeave was able to create a robust and reliable system in just under two weeks.”
— Engineering Manager, CoreWeave
Big AI companies are shipping fast and securely with authentik. So can you.
TL;DR
If you’re tired of:
- Paying for every auth feature behind a paywall
- Relying on black-box identity providers
- Managing five different tools for auth
Then switch to authentik.
🔓 Self-hosted
⚙️ Fully customizable
🔒 Security-focused
💻 Developer-friendly
Try it out. You might never look back at Keycloak again.
LiveAPI helps you get all your backend APIs documented in a few minutes
With LiveAPI, you can quickly generate interactive API documentation that allows users to search and execute APIs directly from the browser.
If you’re tired of manually creating docs for your APIs, this tool might just make your life easier.



















Top comments (0)