Database security in a DBMS involves protecting the data stored in databases from unauthorized access, breaches, and other threats.
It ensures the confidentiality, integrity, and availability of data.
Below, I’ll break down the key concepts mentioned in your query—Authentication, Authorization, Access Control, DAC, MAC, RBAC models, Intrusion Detection, and SQL Injection—with simple explanations.
1. Authentication in DBMS
Authentication is the process of verifying the identity of a user or system trying to access the database. It ensures that only legitimate users can enter the system.
- What it does: Authentication checks if the person or system is who they claim to be, usually through credentials like usernames and passwords.
- Why it’s important: Without authentication, anyone could access sensitive data, leading to potential data theft or damage.
- How it works in DBMS: Users provide login details, and the system matches them against stored credentials. Modern systems may use advanced methods like Single Sign-On (SSO) or two-factor authentication (2FA) for added security.
- Best practices: Use strong passwords, enable 2FA, integrate with enterprise identity providers like LDAP, and ensure passwords expire periodically to reduce risks Few Gold Standard Database Security Best Practices for 2025.
- Example: A company employee logs into a database using their corporate ID and a one-time code sent to their phone, ensuring only authorized personnel gain access.
2. Authorization in DBMS
Authorization determines what an authenticated user is allowed to do within the database. It defines the level of access or permissions a user has.
- What it does: After authentication confirms identity, authorization decides whether the user can view, edit, or delete data.
- Why it’s important: It prevents users from accessing data or performing actions beyond their role, minimizing damage from misuse or breaches.
- How it works in DBMS: The database administrator assigns specific permissions to users based on their roles or needs. For instance, a manager might have read and write access, while a clerk might only have read access.
- Key aspect: It often works with access control mechanisms to enforce rules on who can access what Access Control 101: A Comprehensive Guide to Database Access.
- Example: A hospital database might allow doctors to view and update patient records but restrict nurses to only viewing them.
3. Access Control in DBMS
Access control is a broader concept that includes both authentication and authorization. It’s the set of rules and mechanisms that restrict access to database resources.
- What it does: Access control ensures that only authorized users can interact with specific data or perform certain operations.
- Why it’s important: It protects sensitive information from unauthorized access and maintains data integrity by limiting modifications.
- How it works in DBMS: It combines policies (like who can access what) and technologies (like encryption or login systems) to enforce security.
- Types: Access control can be implemented through various models like DAC, MAC, and RBAC, which are explained below What is Access Control in Database Security?.
- Example: A university database might restrict student access to only their own grades while allowing professors to view and update grades for their classes.
4. DAC (Discretionary Access Control) Model
DAC is a type of access control where the owner of a resource decides who can access it and what they can do with it.
- What it means: In DAC, the person who owns the data or object has full control over granting or denying access to others.
- How it works: The owner sets permissions, like allowing specific users to read or write data, at their discretion.
- Advantages: It’s flexible because owners can share resources as needed without involving a central authority.
- Disadvantages: It’s less secure since owners might make poor access decisions, leading to potential leaks or insider threats MAC, DAC, RBAC, and FGA: A Journey Through Access Control.
- Example in DBMS: A project manager in a company database might grant access to project files to team members but deny access to others, based on their judgment.
5. MAC (Mandatory Access Control) Model
MAC is a stricter access control model where a central authority, not the resource owner, sets the access rules based on security levels.
- What it means: Access is determined by predefined policies and security classifications, often managed by system administrators.
- How it works: Users and resources are assigned security levels (like “confidential” or “top secret”), and access is granted only if the user’s level matches or exceeds the resource’s level.
- Advantages: It’s highly secure because it enforces strict control, ideal for environments like military or government systems.
- Disadvantages: It’s rigid and less flexible, as users can’t override rules set by the central authority What is Mandatory Access Control (MAC)? in 2025.
- Example in DBMS: In a government database, only users with “top secret” clearance can access classified documents, regardless of who owns the data.
6. RBAC (Role-Based Access Control) Model
RBAC assigns access permissions based on a user’s role within an organization rather than individual identity.
- What it means: Access is tied to roles (like “manager” or “employee”) instead of specific users, making management easier.
- How it works: Each role has predefined permissions, and users are assigned to roles based on their job functions. This follows the principle of least privilege, giving users only the access they need.
- Advantages: It simplifies permission management, especially in large organizations, and reduces the risk of over-privileging users.
- Disadvantages: It might not be flexible enough for complex or dynamic access needs Access Control Models: MAC, DAC, RBAC, & PAM Explained.
- Example in DBMS: In a corporate database, an “HR” role might have access to employee records, while a “Sales” role can only access customer data.
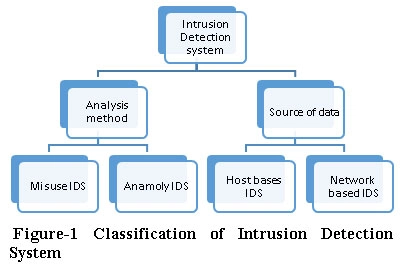
7. Intrusion Detection in DBMS
Intrusion detection involves monitoring the database system for unauthorized access or malicious activities and alerting administrators when such events occur.
- What it does: It identifies suspicious behavior or attacks, like unusual login attempts or unauthorized data access, in real-time or through logs.
- Why it’s important: It helps detect and respond to threats before they cause significant damage, protecting data integrity and confidentiality.
- How it works in DBMS: Intrusion Detection Systems (IDS) use signature-based methods (matching known attack patterns) or anomaly-based methods (flagging unusual behavior) to spot threats.
- Challenges: New attacks might evade signature-based systems if their patterns aren’t in the database, requiring constant updates What is an Intrusion Detection System (IDS)?.
- Example: An IDS in a bank’s database might flag multiple failed login attempts from an unknown IP address as a potential brute-force attack and notify the security team.
8. SQL Injection in DBMS
SQL Injection is a type of cyberattack where attackers insert malicious SQL code into input fields to manipulate the database.
- What it does: Attackers exploit vulnerabilities in web applications or database queries to gain unauthorized access, steal data, or alter records.
- Why it’s important: It’s a persistent threat that can lead to data breaches, financial loss, or system compromise if not addressed.
-
How it works: Attackers input malicious SQL commands (like
'; DROP TABLE users; --) into forms like login fields, tricking the database into executing harmful actions. - Prevention methods: Use prepared statements and parameterized queries to separate SQL code from data, limit database user privileges, and deploy Web Application Firewalls (WAFs) to block suspicious inputs SQL Injection in 2025: How One Vulnerability Can Expose Your Business.
-
Example: A hacker enters
admin' OR '1'='1into a login form, bypassing authentication to access a database, potentially exposing sensitive user information.
At last,
Database security in DBMS is critical to safeguarding data from various threats.
Authentication verifies user identity, while authorization and access control define what users can do, often through models like DAC (owner-driven), MAC (policy-driven), and RBAC (role-driven).
Intrusion detection monitors for unauthorized activities, and protecting against SQL injection prevents attackers from exploiting query vulnerabilities.
Implementing these measures ensures data remains secure and accessible only to authorized users.
Thanks for reading so far.











Top comments (0)